The spectre of BCM has been haunting ‘business’ departments of about any organization for too long. It needs to go away – as spectre, and take its rightful place in ‘Risk’ ‘Management’. The latter, in quotes, since this, this, this, this, and this and this.
Much link, very tire. Hence,

[Opera! Opera! Cala at Vale]
Which actually brings me to the core message: ‘Governance’ [for the quotes, see the last of the above link series again] fails for a fact (past, current, future) if it doesn’t include risk management, and when that doesn’t take this into account:
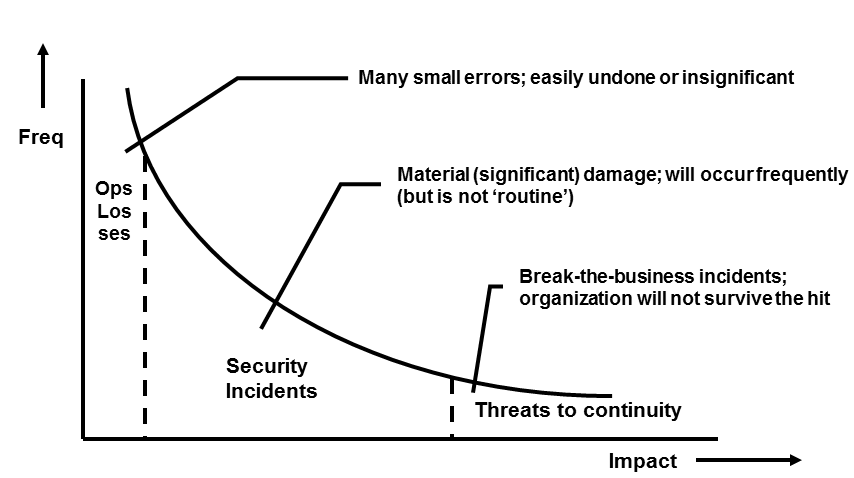
[Here, highlighted for InfoSec as that’s in my trade portfolio…]
First, a reference to that RM-in-Gov’ce mumbo jumbo: Here. (In Dutch, by way of crypto-defeating measure vis-à-vis TLAs… (?)) Listing among others (diversity, sustainable enterprise, external auditor role) the need to do more about risk management at ‘governance’ levels. Which might of course be true, and how long overdue after COSO has been issued and has been revised over and over again already.
But then, implementation … No strategic plan survives first contact with the enemy (ref here). And then, on turf are the wars that be, in all organisations. Among the great multitude of front lines, the one between Information Risk (management) the Light brigade [of which the Charge wasn’t stupid! It almost succeeded but because the commander wasn’t a toff so supporting a brilliant move by such an upstart wasn’t fashionable, he was blamed – an important life lesson…], being overall generic CIA with letting A slip too easily on the one hand, and the all too often almost Zero Business Continuity (management) on the other, outs the lack of neutral overlordship over these viceroys by wise (sic) understanding of risk management at the highest organizational levels. As in the picture: It’s all RM in one way or another. And (though the pic has an InfoSec focus) it’s not only about ICT, it’s about People as well. As we have duly dissed the ‘Process’ thinghy as unworthy hot air in a great many previous posts.
Where’s this going …? I don’t know. Just wanted to say that the IR-to-BC border is shifting, as IR becomes such an overwhelming issue that even the drinks at Davos were spoilt over concerns re this (as clearly, here). But still, BC isn’t taken as the integral part of Be Prepared that any business leader, entrepreneur or ‘executive’ (almost as dismal as ‘manager’) should have in daily (…) training schedules. Apart from the Boy Cried Wolf and overly shrill voices now heard, the groundswell is (to be taken! also) serious: IR will drive much of BC, it’s just that, again, sigh, the B will be too brainless to understand the C concerns. Leaving BC separate and unimplemented (fully XOR not!) next to great ICT Continuity.
Or will they, for once, cooperate and cover the vast no-man’s land ..? Hope to hear your success stories.


















