The fraud triangle should be not more. For too long, the simpleton representation of fraud occurrence possibility has dumbed down the discussion about countermeasures too much, leading to an unwanted, unwarranted, inefficient and ineffective approach difference from various sides.

[For those who know where this is: This is unconnected to the story ;-]
Point being: The fraud triangle, being one where the three factors Motive (or Pressure), Rationalisation, and Opportunity are presented as if present at the same time, and banding together. Take one of the elements out of the equasion and you’re good. But the three factors do not play out at the same time.
Rather, they play out consecutively, leading to a false sense of security when only one is addressed as even the wiki page on fraud deterrence suggests.
Wrongly! Because e.g., when Opportunity is taken away, as if most often the ‘easy’ solution in organisations, Motive and Rationalisation (the formers start it, the latter coaches it) will find another way as the pressure of Motive will rise and rise until somewhere else than the valve installed, some crack or so may burst, or the whole kettle may explode.
[Damn! Here, I had a perfect, really perfect two A4 pages full of text that disappeared in a glitch… The rest you see here, is just a bleak re-do missing the brille of the original… No, the re-write is not better than the original. Thanks, Tumblr! [Insert hard expletives here]]
As Motive is the thing that comes first, it should also be the first thing to address. It starts with not giving too much motive, which is the same as giving all your employees a reasonable compensation for their efforts that starts with the paycheck. In particular in hard economic times, some or many of your employees may heed more to their ethics (!) and provide for their family before sticking to stupid rules of some big anonymous organisation that doesn’t really know who they are and what their pligh is. Ethics, yes, that thought discipline that is about having to decide between the conflicting rules of various groups that any human is part of. Family, friends, etc., and the organisation one might feel part of – or not, or not enough to let organisation group belonging outweigh familiy group belonging when it comes to a showdown, e.g., when they feel they don’t get their due but just the alms you so graciously hand them for your own grandeur only.
And if you’re visible to the public at large (and you will be, however you try to protect your image) as having so much more than your staff has, family etc. may start to actively pressure your employees to get up close to that level. You’re pushing them yourselves! Inequity forces (no, not less than forces) employees into a getting-even motivation..!
Both ‘hard’ and ‘soft’ pressures to get even, play out in the Motive element, but also in the Rationalisation element. Rationalisation is nothing else than the rationalisation of the ethical decision that your unconscious mind already made, for when your consciousness might turn up again later.
Let alone that it may not only be such ethics that force employees into less following the organisation’s stupid little rules. Think of what would happen if a family health or life is threatened by rogues; this happens all the time. But you can’t have all your employees and their family being secured all the time; they will leave you all as no-one can life under such circumstances of total siege.
And you do need to care for all employees, as all have access to possibly Opportunity-instrumental information. Do not think that you org chart or top-down approach may work, at all. That would miss (literally) 99% of all the information flow that goes through your organisation, and 99% of the paths that the information takes. You think your ‘processes’ are your organisation? Think again, think the opposite!
Which ties in with the Opportunity part. The Opportunity may be everywhere, at all organisation levels, in all sorts of combinations of petty-little-rule breaking or ‘sticking to the little rules so you can break the big ones’. You simply cannot know all the ways and places, and times, that Opportunity for fraud may exist. If you think that simple things like encryption may help then yes, they may help, but so little, so very, very little. As if IT staff, and masses of others, would not know their way around it. And any dam creates its lake that will overflow and create much more damage; the pressure is not diminished by the dam!
So, you can’t do much about Motive, Rationalisation, or Opportunity. Not much, a little bit.
Which is where we may take a look outside of the totalitarian control bureaucracy world I led you into above, which is typically today thinly veiled under a ‘Risk Management’ layer (just this morning saw an article discussing that we don’t need Risk Management, we need management of risk…!], or under the label ‘risk-driven information security’ etc. All wrong approaches, panicky seeking total control.
All we can do, then, is to sand off the rough edges. Which is what is done already, by (physical) Security as it has been done through the ages. Just take a look at a sample table:
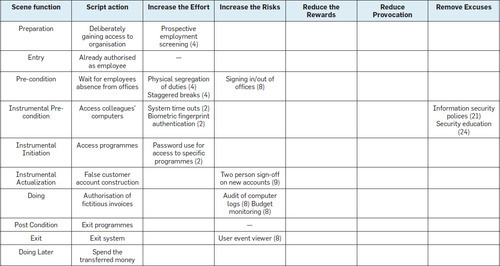
It’s easy to see how this can be filled in to cover many more angles and available tools of information security, and can be expanded to cover much more of your organisation’s business. And it’s also easy to see that e.g., not all information security should be had only from IT measures, and not all process/procedural opportunity should be lessened by procedural refinement only. Cross-discipline measures could keep it all much lighter!
But just look at the last five column headers… Much better to approach fraud prevention through those than just sticking to Motive, Rationalisation, Opportunity, right? These ‘solutions’ may not prevent each and every fraud, but they keep things in check. If that’s the most you can get, then be happy with it!
More, maybe, later, on filling out the table in all sorts of situations.















