Oh, I’ve been outdone again, in some ways. Which isn’t a big deal; ’twill happen to you, often, too. This time, it’s about the IAM in IoT that I signalled here and here, here, and here as a generic problem. Correct: Challenge.
Which all was readable. Hopefully. For all dealing with the stuff on a monthly basis (ahum, ‘weekly’ or ‘daily’ wouldn’t make sense; you’d be ahead of me probably…) that is. For a more general explanation, one can now turn to this here piece; much better at generalpublicspeak than I’d produce when diving onto it again.
Oh well. This:

[Somehow, typically Madridean ;-| / Southern European / Latin style]
Category: Privacy
All against all, part 6; loose ends
OK, herewith the final-for-now Part VI of the All Against All matrix-wise attack/defense analysis labeling. This time, about tactical content of … mostly, the defense matrix of edition IV.
Where I wanted to do a full-scope in-depth analysis of all the cells of Matrix IV. Not the sequel but the actual original defense posture strategy matrix. Because that was put together in a straightforward sloppy way anyway.
But then… I wanted to detail each and every cell according to this here scheme:
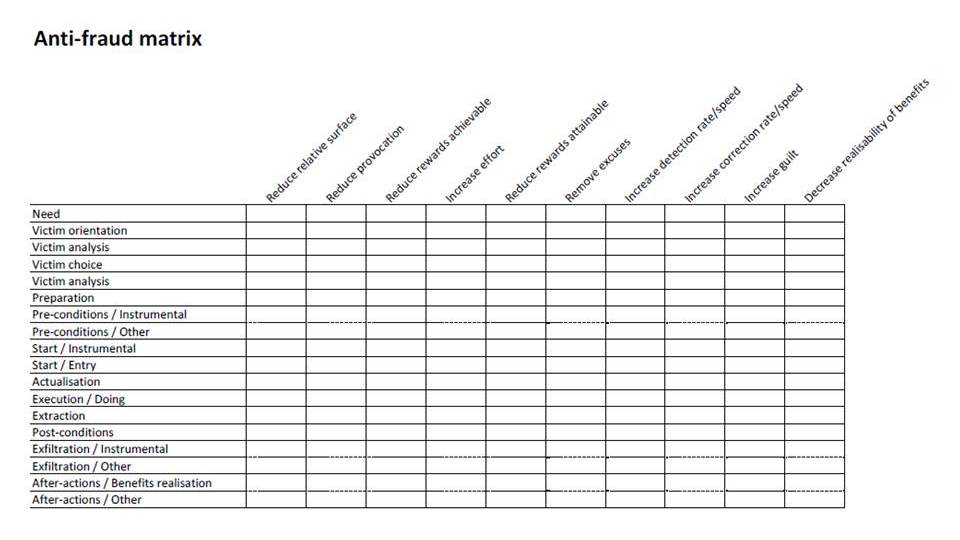
After further analysis along the lines of this here approach:
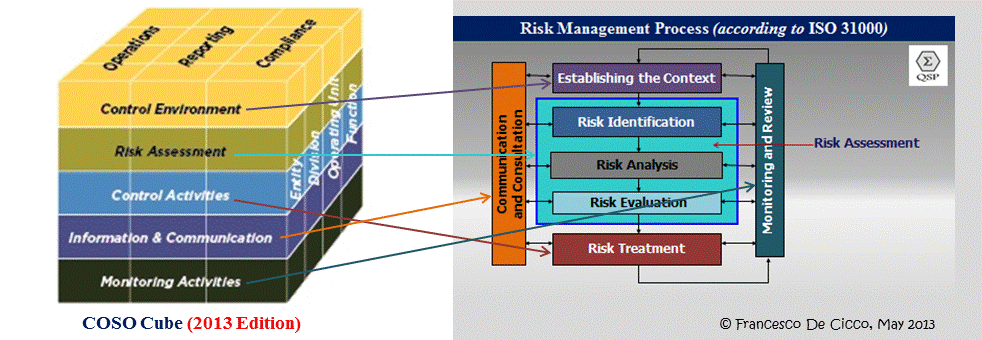
but mixing that quite hard, according to this previous post of mine (certainly the links contained therein, too) and a great many others contra bureaucratic approaches… but also mixing in the guidance of (not stupid compliance with!) the new one that at last, has quite some ‘user’ involvement in it. But still is based on both the top-down and the step-by-step fallacies a bit too much.
But it’s late and I don’t feel like the tons of effort involved. Yet. Maybe in a future enormous series of posts …
And should include references to OSSTMM here, too. Because al of the above, in the super-mix, will have to be checked and sensitized (is that the word for checking that it all makes sense?). Short of the word ‘audit’ where the respective profession (a trade, it is… at most, a role) has let us down so much. If only by the kindergarten zeal about ‘governance’ and ‘value’ – phrases so hollow (or circularly defined) that they’re not worth the ink (light) they’re written with, when used in the auditors’ contexts.
So, OSSTMM may help. By inspection where the rubber meets the road. And fixing whatever needed to be. Duct taping the last few bits, where the beautifully AutoCADded [anyone remember what that was (for)!?] frameworks failed in the machine milling. Or 3D printing, or whatev’, due to design failures due to requirements failures due to failures in common reason at the upper levels…
Now, with all the all against all posts (1 to 6 indeed), would you be able to advise Sony, and the others, how to be better protected ..? You should. Or re-read the whole shazam until you do…
After all of which you deserve:

[Cologne, of the massive kind]
The Pirate Bay to Source Pay à le Lanier
… it may they say [title because reasons]
Well, this just struck me. If the Pirate Bay, back up since a couple of weeks, could innovate, this could be one avenue. Implementing the ideas of Lanier’s You Own The Future to attach original-source coding (not as in a programming language but as location (?) IDs) – and automatic microcopyright payments… – to creative works. Somehow, it would feel right if the PB would implement such a thing.
Voluntarily, to show they’re not Bad Guys. And don’t cave in all the way à la Napster, and innovate beyond Spotify.
Your comments, please. In return for:

[Maybe not Great but still quite passable, worth(while); sorry 416]
All against all, part 5; discussion
OK, herewith Part V of the All Against All matrix-wise attack/defense analysis labeling. Let’s call it that, then.
Where the big move in the matrix is, of course, from the top left half towards the bottom right half. Where there’s a continuation of politics by other means. At a grander scale, the analysis (or is it synthesis..?) turns to:
- The resurgence of, let’s call it, Digital Arms’ Race Cost Competition / Collapse. Just like the old days, where economic and innovation attrition was attempted by both sides of the Cold War. Including the occasional runaway tit-for-tat innovation races and some flipping as well. Yes, all the mix applies.
- The analysis that the world (yes, all of it) over the decades and centuries seems to bounce on a scale between a bipolar 2-giant-block stand-off on one hand, and a 1 giant versus multiple/many opponents on the other. Like, Europe has oscillated between such positions over the centuries. And took them global by enlisting their youngest sibling (as Baldr to the rescue), the half-god saving the others from Ragnarök, the USofA – against the hordes from the East as predicted by our dear friend Nostra da Mus (remember? though he had a diferent view on the ideology involved…) In Da House. Now that the global stand-off had reached the DARC stage, we see a multi-opponent scheming and chessplaying once again. USofA, EU still somewhat attached but …, Russia and Friends, China, India, Brasil and friends, a host of semi-independents in the East and Far-East, and in the Middle-East (what’s with the Middle, if centers of power gravity change and disperse so quickly?).
Edited to add: This Attali post, basically delineating the same. - As usual throughout human history, it’s the underlings and meek dependents all throughout the top left three quarters of the matrix that are war zones and battle grounds, too, suffering and being sacrificed as pawns without too much share of the spoils, profits, trophies and laurels. For the skirmishes and all-out war’lets as the 20th century shows.
- Still somewhat ethics-bound players (e.g., “democratic” (quod non) countries) will also have to fight internally, for legitimacy of their ulterior objectives (externally, internally), strategies, tactics and operational collateral damage. Which in turn binds them down tremendously, when up against less scrupulous players. Don’t wrestle with pigs because you both get dirty and the pigs love that. Unless of course you’re fighting over the through’s contents for survival. And you have one hand tied behind your back, internally, while fighting for the greater good of all, externally.
So far, so good. Much more could be said on the above, but doesn’t necessarily have to. Because you can think for yourselves and form your own opinions and extensions to the above storylines, don’t you?
Still to come: (probably the 18th) a somewhat more in-depth view on the matrix of part V, going deeper into the defense palette.
And indeed, I’m still not sure this all will lead anywhere other than a vocabulary and classification for Attribution. But I see light; an inkling that actually there may be value and progress through this analysis …
After all of which you deserve:

[Grand hall of the burghers. I.e., the 0,1% …; Brugge again]
All against all, part 4
OK, herewith Part IV of:
Tinkering with some research that came out recently, and sometime(s) earlier, I had the idea that qua fraud, or rather ‘Cyber’threat analysis (#ditchcyber!), some development of models was warranted, as the discourse is dispersing into desparately disparate ways.
The usual picture suspect:

[Mock defense, open for business at Brugge]
Second up, as said: The same matrix of actor threats, (actor) defenders, but this time not with the success chances or typifications or (read horizontally) the motivations, or typical strategy-level attack vectors, but basic, strategy-level defense modes. Not too much detail, no, but that would not be possible or the matrix would get clogged with all the great many tactical approaches. Those, laterrrrr…
Next up (probably the 16th) will be a discussion of movements through the matrix, matrices (by taking both the blue and the red pill; who didn’t see that option ..?), for state actor levels. And (probably the 18th) a somewhat more in-depth view on the above matrix.
Hmmm, still not sure this all will lead anywhere other than a vocabulary and classification for Attribution (as in this piece). But I see light; an inkling that actually there may be value and progress through this analysis …
All against all, part 3
OK, herewith Part III of:
Tinkering with some research that came out recently, and sometime(s) earlier, I had the idea that qua fraud, or rather ‘Cyber’threat analysis (#ditchcyber!), some development of models was warranted, as the discourse is dispersing into desparately disparate ways.
The usual picture suspect:

[What no throwback to the socialisixties ..?]
Second up, as said: The same matrix of actor threats, (actor) defenders, but this time not with the success chances or typifications or (read horizontally) the motivations, but with typical strategy-level attack vectors. Not too much detail, no, but that would not be possible or the matrix would get clogged with all the great many tactical approaches (including social engineering, spear phishing, etc.etc.).

Next up (probably the 12th) will be typical countermeasure classes.
Hmmm, still not sure this all will lead anywhere other than a vocabulary and classification for Attribution (as in this piece). But I see light; an inkling that actually there may be value and progress through this analysis …
Coolness 1 – progress 0
Hm, on the face of it, this here is interesting: the director of Europol (no less) saying that TOR and Bitcoin shouldn’t be vilified even if they pose problems for agencies, since they allow cittizzzens to enjoy the freedoms of the Interwebz.
Nevertheless … Claiming that means: ‘may still be needed to trace and convict those colouring outside the boxes’, which would raise suspicion of window dressing. Let’s see how this talk will be walked, shall we ..?
Repudiation, repudiation (not) everywhere
With DARPA’s quest for Active Authentication (as here), what will the future spread of (non-)repudiation look like ..? By means of strength of proof e.g. before courts, when system abusers may claim to accidentally have the same behavioural ICT use patterns as the unknown culprits, or be victims of replay attacks.
I’m unsure about how this will play out, then; whether Innocent Until, or Proof of Innocence, or even Reasonable Suspicion may still exist.
Yeah, I get it – you’ll claim that this is for DoD purposes only. Of course, as it never has, in the past. @SwiftOnSecurity would (need to) be on the alert.
Well, as this kind of innovation (by this agency) usually reaches society in all sorts of very unexpected ways, there’s hope that something in support of the Constitution may in the end come out… for now, I’ll leave you with:

[Light on the inside, though without outlook… FLlW at Racine, WI]
To study; unconscious compliance, conformity
A quite good analysis here, of this book.
Which throws a wrench in many discussion positions for or against privacy … also in the light of this book. Are we numb mindless drones in larger schemes, or are we individuals whose choices happened to coincide? Through availability of emergent too-selective alternatives or what?
Think about that. And revel at:

[Cheney interior, original. And B&B ..! Hey don’t complain, ‘t is from an analog one again, circa 1997.]
Start the Told You So now you still can (?)
Against the trend to dismiss any dystopian view as unduly unoptimistic and hence invalid, that I so dislike..: This here piece by In the Knows.
The Told You So Boys Cried Wolf (lopping two memes into one, in this case appropriately) may better have started now, since they will not be heard (fact about the (near) future) and may not get another opportunity when all the others, the drones, have been subdued by the 0,1%, the AI singularity beast. To put it mildly ;-|
Or, … maybe this time around, some exponential counter force may have come off the ground – not yet into full above-the-radar-floor visibility but still… If ever in history there was a chance to get it (technology) right, it would be now, now that more people are in the middle class (that always takes the beating, apart from the continuous light flogging the underclasses have always got and will always get) and have just the right minimum levels of insight and might care for their future. Unprecedented as an opportunity but hardly assured it’s seized…
Anyway…, this:

[Strasbourg, astronomical clock – yes, science within a cathedral]







