
[From Riga, for you]
For a real update on my Prediction for 2014 (see below some post, and the original post), I homage Ross Dawson for a much better long-term rationale.

[From Riga, for you]
For a real update on my Prediction for 2014 (see below some post, and the original post), I homage Ross Dawson for a much better long-term rationale.

[Unseen Rotjeknor]
In the stories on Big Data et al. (predictive analysis, … , you name it), I often see a big confusion about terms. Some even mix up data and information, or only pay lip service to the fundamental difference..!
Oh yes, many come up with the Information Pyramid; in a most basic picture I took from wipo.int:
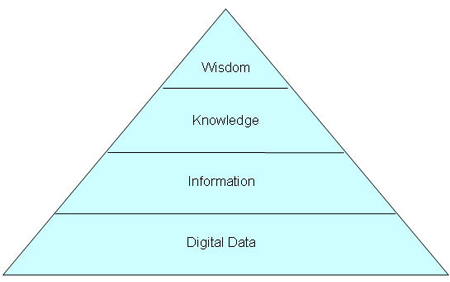
* sometimes, Knowledge is bracketed between Data and Information; more on that below.
But there’s something fishy with the way the picture is being used, commonly.
For one thing, any action that produces meta data (i.e., just plain flat derivative data !!) is considered to be ‘enrichment’ onto Information. But that’s wrong! All the aggregation, the averaging, the abstraction that you do, only delivers other data, with the (near-mathematical) translation functions still intact – although also, information gets lost..! Yes, the details count, and have their own ‘information’; a full description of all data points in a set would require at least all the data points themselves, or miss something when they’re described, circumscribed otherwise.
The problem is; no-one really knows how to get from Data to Information as we intuitively (heh) understand it. Information seems to be detached, or separated from Data by a chasm that we do not know how to cross, probably because our understanding of what Information is, and our definitions, are so weak.
Oh, and putting a layer of Knowledge in between Data and Information, doesn’t help anything, either. Even worsens the problem. As it is above, it doesn’t say much either. And instead of Knowledge, above one could also fill in Understanding, or Insight (which would come closer to but remain separated from Wisdom). And above the peak, is there Nirvana? Smells like blog spirit.
So, all the efforts of NLIQ and MITIQ may be fine, as for data analysis to try to achieve predictive analysis (nice pun, the contradictio in those terms!), but as long as Data and Information are used arbitrarily (see the list of publications and the actual articles contents …), one will remain stuck in data analysis and not reach the next level of Information. Or Knowledge, let alone Understanding, Insight or even Wisdom.
But I keep running in circles. Yes, I know, and I also know that in order to advance, we’ll need to get a grip on two things:
1. Definitions, in the traditional sense or by way of aspect/category/label/hermeneutic quality descriptions, of all the levels we may distinguish;
2. Definitions, in both ways, too, of the transitions and transition methods, tools, etc., we may construct theoretically and practically.
I’ll do some work on this, but your help is appreciated..!

[Antwerp. Seriously.]
In some previous post, I posited that we should move from quantitative (quod non) to qualitative or even intuitive risk management.
And how that may be difficult. ‘cause it is.
As an intermediary step, I propose to build a better language with which to communicate, discuss and calculate (sic) with qualitative risk management.
Because I see a place for a combination of fuzzy logic and wavelet theory, including neural network signal combination functions.
As my time is limited, this time of year, would anyone have pointers to what’s already out there in papers, practical applications, etc..? That could kickstart the discussion. And I’ll return with more, better, more extensive, more thought out stuff on the subject later.

[Guess the location]
Your digital ID becomes your pseudo-identity becomes who you are (considered to be), more than your actual you.
Your actual you, your innate identity, the one you discovered when only a couple of years old, will no longer be of interest to the world once your digital identity has all that the world cares about. Then, it can get stolen, lost, manipulated and altered, without you actually needing to notice. But who cares? Your digital ID is, you are just the carbon-based remnants of an outdated world. Just make sure there’s a fallback scenario that you can (or wouldn’t need to) prove you are you, your digital ID isn’t you.
The singularity may do away with you because you only use up scarce resource. You are not productive, your digital identity is. So you should care. Or?
If social media use ‘you’ as a resource, uses your apparent digital ID (ID and all posts, tweets, etc., turned into a persona, sold to all bidders) to operate, can you not deploy some artificial intelligence mechanism to do the socmed postings on your behalf ..? What’s the difference to the socmed companies that not your brain, but an artificial brain is used ..? Or do they already have their own farms of AI personas, to beef up traffic and sellable ‘user’ generated content ..?
Their AI personas may create a world separate from yours, a virtual world where they make money, not needing actual users anymore.
Your personal self may deploy AI to detach from their abusive, you-usurping world.
Case closed?

In the discussions re privacy, there seems to be only two alternatives: Absolute privacy, with any individual holding complete, total and continuous control over who gets to see (not take in) any data point that may be, even in the remotest of ways, be recombined into anything useful for anyone – or Absolutely no privacy, everything being considered lost anyway and all one’s data being out there somewhere.
Which creates not some binary future state, but a bandwidth on which we should be able to choose. Because it is not privacy that people are concerned about, but the loss of control once data slips out of your hands. That is why everyone is so concerned when TLAs are found out to collect so much data on everyone (they have tried, and partially succeeeded, already for decades; nottoo many people were concerned) or when (not if) yet another credit card data processor looses some backup tapes. It is not the privacy in itself (one passes off the credit card number (and CVC) happily to just any unchecked device), it is not being able to get the data ‘back’, not being able to track the use in all the enormous amount of systems one knows is out there handling your data. Those systems ranging all the way from the benign to the crooked, always …
What we should have, then, is some mechanism by which we would be able to transparently and trasitively (sic) release the data we must (in order to get some service in return), and be rewarded for any data other parties earn money with (they are using your resource!), and not more. We’ll have control back; all we wanted.
Anything else, and we’ll end up in one of both extremes. To our own extreme detriment.

[Educational institute x 3, campus Free University, Amsterdam]
When sleeping over problems, one often comes up with solutions that both are real and so all-encompassing that they’ll need much elaboration before being applicable in a nimble way.
This one was/is on information security, again. Recall the ‘discussions’ I posted some days ago about (industrial) process control versus administrative control? Well, I’ve some more elements for a grand new scheme now.
It struck me that the operators at the (chemical) plant control room, are the ones with the dashboards. Not necessarily their managers. Nor their manager managers, etc. What if instead of some machine equipment, we plug in hoomans into the whole ..? And let them interact like the übercomplex ‘machines’ that they are, doing their (administrative / service) thing that they (want to?) do. All the way to the point where we have no equipment, just humans (with tools, by the way, but those would be under ‘complete’ control of the ones using them so are just extensions of them). One ‘manager’ could then control quite a lot; have a huge span of control…
If, big if, if only the manager would understand the overall ‘process’ well enough, that is, to be able to work with the dashboard then provided. Just Continuous Monitoring as a job, not much more (one would have 2nd- and/or 3rd ‘lines of control’ (ugh for the expression) to fix deviations, do planned maintenance, etc.). Probably not. But one can still dream; organizations would be flat without chaos breaking out.
And if you’d say it would be impossible altogether, have a look at your SOC/NOC room where techies monitor IT network traffic and systems’ health. They even have some room to correct..! And they are aware, monitor, the appropriateness of what flows over the lines, having professional pride in catching un(machine)detected patterns of irregularity possibly being break-in/break-out attempts. And they leave the content for what it is, that’s for the experts, the users themselves, to understand and monitor if only they would.
Why wouldn’t other ‘managers’ copy the idea to their own desk? No, they don’t, yet. They get Reports that they hardly read, because someone else had thought for them in determining what should be in there. And reports aren’t continuous. Walking around is, but would (rightly) be viewed as micromanagement and a bit too much given the non-continuous nature of what modern knowledge workers do. So, we’ll have to define some gauges that are monitored semi-continuously.
Now, a picture again to refresh:

[Westpunt, Curaçao]
But with the measurements not influencing the primary production ..! To let knowledge workers do their thing, in mutual cooperation without interference by some busybody thinking (s)he knows better for no reason whatsoever.
Through which we note that the use of dashboards should not, must not, start with ‘Board’s or similar utterly superfluous governance levels. Governance is for governments. As it is ‘implemented’ in larger organizations, it doesn’t look like kindergarten kids playing Important for nothing. The use of dashboards should start from the bottom, and should include quite rigorous (but not merely by the numbers) pruning of both middle-level ‘managers’ (keep the good ones, i.e., not the ones that are only expert in hanging on! otherwise you spell death), and all sorts of groupie secondary and third-line staff.
Which will only work if you haven’t yet driven out all the knowledge workers by dumbing down their work into ‘processes’ and ‘procedures’ that are bereft of any productive (sic) rationale. And if you haven’t driven out all the actual managers and are left with the deadwood that is expert only in toeing the line or rather, sitting dead still in their place.
Now have a look back also on how you do information security. Wouldn’t the little bit of tuning you may need to do, be focused best on the very shop floor level that go into the ‘industrial’ process as inputs? You would only have to informationsecure anything that would not be controlled ‘automatically’, innate in the humans that handle the information (and data; we’ll discuss later). Leave infosec mostly with them, with support concentrated at an infosec department maybe, and have managers monitor it only to the extent necessary.
And, by extension, the same would go for risk management altogether. Wouldn’t this deliver a much more lean and mean org structure than the top-down approaches that lead to such massive counterproductive overhead as we see today? With the very first-line staff that would need all the freedom feasible to be productive (the managers and rest of the overhead, aren’t, very very maybe only indirectly but certainly not worth their current income levels!) then not having to prove their innocence… See Menno Lanting’s blog for details…
Org structures have become more diamond- than pyramid-shaped; which is plain wrong for effectiveness and efficiency…
So let’s cut the cr.p and manage the interfaces, vertically, and horizontally, noting the faces part; human. An art maybe, but better than the current nonsense…
Already somewhere below, I noted that the Analytics part of SMAC(T) may need to be rephrased. Already now, I’m unsure whether to do that or just leave it unchanged. What I didn’t yet do, was to opine on the other elements so often put together.
First, a picture.

[Casa de Música Porto, for the chaotic structure of the future]
Now then:
Social everything: Yeah, yeah, of course there will be news. The decline of Fubbuck, etc. But will we see actual breakthrough hitherto unseen inventions of anything game-changingly new? I predict 2014 will be a pause year in which we’ll only see paradigm detailing and quite an improvement (sic) of the use of Social by medium- and larger sized enterprises. In somewhat innnovative ways, but nothing earth-shattering.
Mobile everything: The same, hopefully through the much-wanted huge improvements in cross-platform and cross-screensize compatibility and standardization. Which, too, would be refinement rather than absolutely unexpected New.
Analytics, we discussed, separately.
Cloud, ‘mehhh’ for theory, ‘hey how refreshing to be able to distinguish so clearly a good implementation’ in practice. Because that’s what we’ll see in 2014; cloud stuff deliberately done right. (Being deliberate, not by accident as it was in 2013!)
Things; The Internet Of ~, maybe, but in my view it’ll be too early. More like something for under the [Warning: European + derivative culture reference coming up] Christmas tree, to be played with in the year after.
Any other business?
Yes.
One with long odds: Clarity on the demise of “ERP” software. Of course, pre-2014 already the said administrative software, hardly ever used to its full potential but very often having been relegated into the bookkeeping role only, had been pushed away from the limelight into the back of the stage. But in 2014, we’ll see an acknowledgement of this, with consequences I cannot really predict very well – probably, all sorts of other software, more geared towards front-office functionality and integrating better architecturally with the bandwidth from there to the app/widget-world, will take over center stage.
[Update 2014 02 06: This link]
One with lesser odds: An enormous push for more information security, both at its operational, technical levels and upwards in renewal of structure (away from the stale, outdated ISO2700x sphere!) and inclusion of a more holistic approach (see some of my earlier posts, and probably some to come in the near future).
This will have a second leg in renewed interest in Business Continuity Management, not only by rule-based following of standards but also by more principle-based (sic) implementation of ISO 31000 (with all its drawbacks) throughout the business. If we can get our heads around the eradication of that ‘the business’ nonsense… and really integrate (continuity) risk-based management into general management, not needing too much 2nd or 3rd lines:
A final one: The deflation of TLD. The three lines don’t actually defend against anything but regulatory discovery of all that goes wrong in the business (from top to bottom and back again, there). As the previous prediction will already defend against actual mishaps, TLD will be shown to be emperor’s new clothes where lightning strikes. And oh will it strike; frappez, frappez toujours! it will and I hope. All those busybodies doing busywork, I just can’t stand it. The utter denouncement of humanity and human dignity …!
So, there you have it again; SMAC(T) weighed, and three more. Who make some interesting stuff available when I hit (or overshoot) five or more out of eight ..?
To close, another picture…

[Serralves, Porto – rainy outlook]
Before I forget: Some work has been done indeed on translating the industrial process (control) model to the administrative world. ACS’s KAD+ model (in Dutch) is an excellent example – especially the original KAD model at operational level that seems unsupported now. Maybe they are just a bit too far ahead of the curve, too clean-cut, to have found the traction they deserve.
That’s all, folks!
For now. Here’s a picture for your viewing pleasure:

[Alhambra, Granada]
Yeah, next up, some seriously long form blog again.

[Unfamiliarly, from the West]
The end is nigh, of 2013. Can we predict what the big business / infosec hype of 2014 will be ..?
No. There’s no predicting the unknown. The somewhat-known will not stand out enough. The known… boring!
The knows are the fall of Fubbuck, maybe Tvitter (both to be replaced by the WeChat’s and hopefully Tumblr’s of this world; will Vine and Snapchat take over?), cloud, BYOD/flexwork, etc.
SMAC: Social, Mobile, Analytics, Cloud. ViNT by Sogeti adds a T of Things.
The Things part, I’m unsure about. Yes, for the long run (i.e., 2-5 years) we will definitely see an explosion. But next year already? It’s the infancy of a sine wave, taking off slowly.
So, my prediction is that the thing we’ll all be talking about as the next thing in 2014, would be … People versus Algorithms.
This was pointed out by some #Coney guy(s), with some lead links elsewhere. But algorithms will not conquer the world in one swallow. Rather, we will see both an increase in the use of algorithms for partial (at most!) data analytics, to support TLA-style use of ‘big’ data both in public and private environments – but also a major development of the People component in tha analysis, a wave of development of specialized functions, methodology and tools, re the human pattern detection and interpretation parts of analytics.
Plus, then a more clear picture of how people and algorithms fit together, as function, profession(s), etc., with spin-off everywhere e.g., the development of a better understanding of how the brain works, how humans work (produce / operate), how to describe the purpose of life. On our way to the Singularity, and Beyond!
Just a question: Would anyone know some definitive source, or pointers, to discussions either formal or informal, on the logic behind double secrets i.e. situations where it is a secret that some secret exists ..?
Yerah, it’s relevant in particular now that some countries’ government seems to have failed to keep that double secret completely, but should be more systematically dealt with, I think, also re regular business-to-business (and -to-consumer) interactions.
So, if you have some neat write-ups of formal logic systems approaches, I’d be grateful. TIA!