When discussing Privacy, a lot of attention goes to informational privacy, easily tautologised with person-possibly-indentifying data.
If that reads mixed-up, it’s because it is.
But that’s for another session series. Of series.
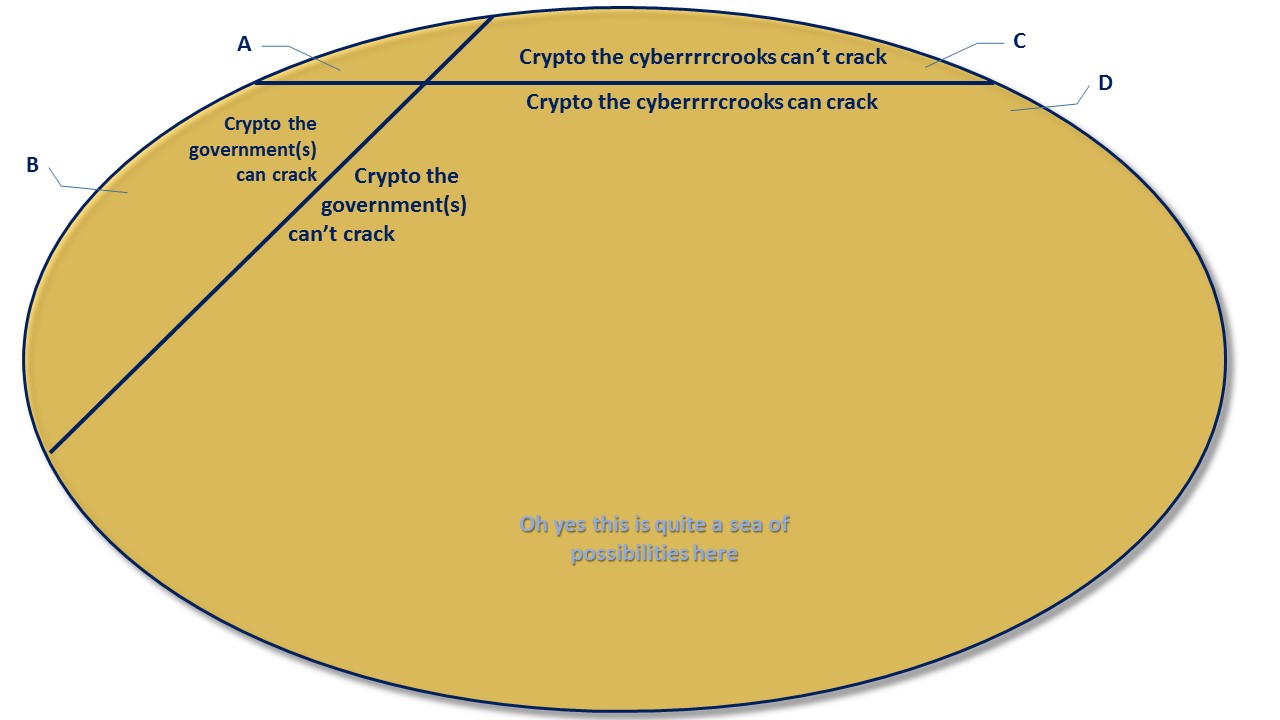
What today’s post title is about, is the distinction between the two sides of the house; informational privacy (which is about information about you, or which you generate) versus decisional privacy (commonly defined in terms of your right to freely decide over your body’s integrity). As you read that, clearly the latter needs an update; a heck of a long KBxyzuvw article attached.
Because both the
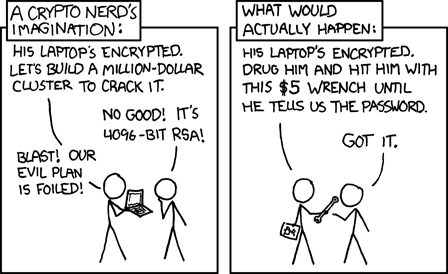
- Outright choice limitation through covert or overt profiling and covert or overt automated decision making, sometimes limiting your choice to none when you get rejected (from the ability to even decide) for something, or get no service proposition at all, a.k.a. the Hobson’s choice of socmed,
- Covert choice limitation through filter bubbles – which would more accurately be called filter fish-trap,
can result from a lack of informational privacy. But both aren’t well covered in the definition of decisional priv whereas that infamous thing with The Freedom of the Pursuit of Happiness or whatsitcalled I don’t care you get it, Freedom, should be guaranteed.
So tightly coupled with all sorts of metaphysics, ontology, and topology of Privacy. Like, the feeling and understanding y’all have when you hear that word. It’s not only ‘bugger off nothing of your interest here’ privacy but also ‘get off my back‘ privacy; no weighing down.
Oh well. This being among my interests but not really my training, so I’ll go read up the latest qua this all. Pointers appreciated. And:
 [For no reason whatsoever, totally unconnected; Riga Jugendstil]
[For no reason whatsoever, totally unconnected; Riga Jugendstil]