Ah. Actually, I needed a well-ordered list of the subset of my posts re All Against All. Because searches don’t pony up the rightly ordered results, herewith for future reference:
So… Done. For you:

[Well-calculated dare, Madrid]
Ah. Actually, I needed a well-ordered list of the subset of my posts re All Against All. Because searches don’t pony up the rightly ordered results, herewith for future reference:
So… Done. For you:

[Well-calculated dare, Madrid]
Recently, there was yet another exepelainificationing of ‘software defined networking’, along the lines of separation of the control plane from the data/content plane (here).
Which ties into a core problem, with IoT the subject of this post: Integrity.
Yes, confidentiality may be an issue, but singular raw data points themselves often are too granular to actually steal any information from. And Availability is of course also of the essence, especially in ‘critical’ systems. But te main point of concern is with Integrity, of the system in a wider sense, but also in the smallest sense.
Take Stux … Integrity breach as the vector space, spanned along a great number of dimensions.
Objective: Degradation of the information value; increasing the variance to a level where noise overwhelms the R2 of the signal (however far from log2(n), big if you understand), through degradation of the (well, original) software integrity.
Path: Introduction of intentionally-faulty (?) software. With use of of, probably, penny-wise correct IAM, being pound-foolish at the medium level. I mean, the level where human and other actors are unwitting accomplices in planting da bomb. That’s what you get by simpleton top-down compliance with just about every thinkable rule: To do any work, underlings will devise ways to circumvent them. And, adversaries will find, see, avenues (that wide) for riding on the backs of the faithfully compliant to still achieve the objective.
But OK, back to … separating the control plane from the data plane. Bringing a shift in efforts to disrupt (no, not of the mehhhh!! destructive, economy-impoverishing kind but in the actual signal degradation kind) from just-about any attack plane down to, mostly, the control plane. That may seem like an improvement, de-messing the picture. But it also means shifting from a general, overall view of vulnerabilities to the core, and a core which is less tested or understood, and harder to monitor and correct, than previously. Or is it ..?
So, if we take this Software Defined to IoT, we’ll have to be careful, very careful. But yes, IoT is constructed that way … With signals to actuators that will result in altered sensor data feedback. Know the actuator signals, and the actuator-to-sensor formulas (!), and you’re good to go towards full control, with good or bad (take-over) intent. Know either (or how to get into the sensor data stream), and at least you can destroy integrity and hence reliability. [DoS-blowing the signal away in total blockade or grey noise wipe-out, and your cover is blown as well. Is a single-shot or semi; you may want to have full-auto with the best silencer available…]
Hm, the above from the tinkering with the grand IoTAuditing framework promised… To turn this all into a risk managed approach. Well, for now I’ll leave you with:

[It has a glass floor up in there, you know. Blue Jays territory, ON – and yes, a very much sufficiently true and fair horizontal/vertical view picture, according to accountants]
Well, whatever percentages in this; Voltaire was right. Even if there would be just one citizen who’d think otherwise, all others should (also) defend his (her?) right to be wrong, to the death.
As it’s already five o’clock (here), have a nice weekend, with:

[Not quite St.Pat’s Day material, still quite equivalent of the Green … Frankenmuth, MI]
OK, herewith the final-for-now Part VI of the All Against All matrix-wise attack/defense analysis labeling. This time, about tactical content of … mostly, the defense matrix of edition IV.
Where I wanted to do a full-scope in-depth analysis of all the cells of Matrix IV. Not the sequel but the actual original defense posture strategy matrix. Because that was put together in a straightforward sloppy way anyway.
But then… I wanted to detail each and every cell according to this here scheme:
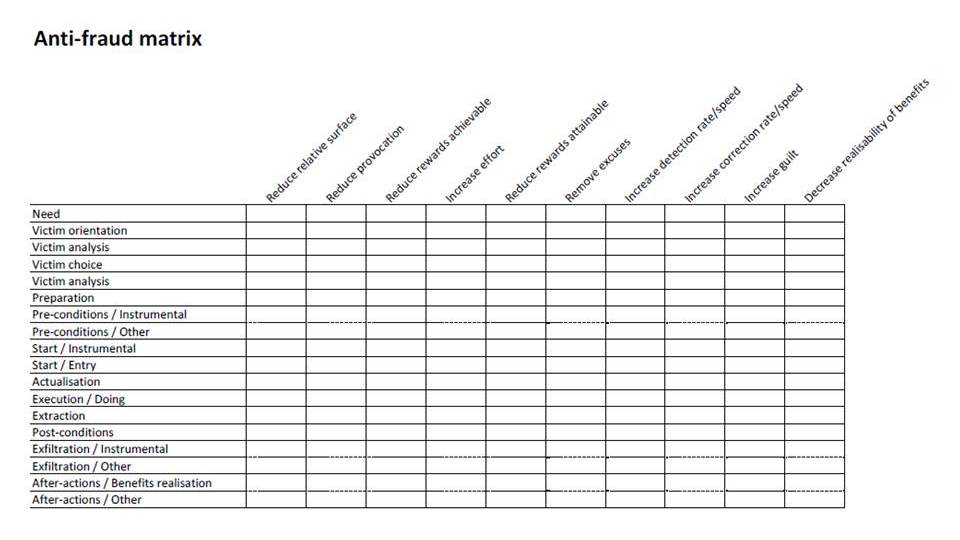
After further analysis along the lines of this here approach:
but mixing that quite hard, according to this previous post of mine (certainly the links contained therein, too) and a great many others contra bureaucratic approaches… but also mixing in the guidance of (not stupid compliance with!) the new one that at last, has quite some ‘user’ involvement in it. But still is based on both the top-down and the step-by-step fallacies a bit too much.
But it’s late and I don’t feel like the tons of effort involved. Yet. Maybe in a future enormous series of posts …
And should include references to OSSTMM here, too. Because al of the above, in the super-mix, will have to be checked and sensitized (is that the word for checking that it all makes sense?). Short of the word ‘audit’ where the respective profession (a trade, it is… at most, a role) has let us down so much. If only by the kindergarten zeal about ‘governance’ and ‘value’ – phrases so hollow (or circularly defined) that they’re not worth the ink (light) they’re written with, when used in the auditors’ contexts.
So, OSSTMM may help. By inspection where the rubber meets the road. And fixing whatever needed to be. Duct taping the last few bits, where the beautifully AutoCADded [anyone remember what that was (for)!?] frameworks failed in the machine milling. Or 3D printing, or whatev’, due to design failures due to requirements failures due to failures in common reason at the upper levels…
Now, with all the all against all posts (1 to 6 indeed), would you be able to advise Sony, and the others, how to be better protected ..? You should. Or re-read the whole shazam until you do…
After all of which you deserve:

[Cologne, of the massive kind]
OK, herewith Part V of the All Against All matrix-wise attack/defense analysis labeling. Let’s call it that, then.
Where the big move in the matrix is, of course, from the top left half towards the bottom right half. Where there’s a continuation of politics by other means. At a grander scale, the analysis (or is it synthesis..?) turns to:
So far, so good. Much more could be said on the above, but doesn’t necessarily have to. Because you can think for yourselves and form your own opinions and extensions to the above storylines, don’t you?
Still to come: (probably the 18th) a somewhat more in-depth view on the matrix of part V, going deeper into the defense palette.
And indeed, I’m still not sure this all will lead anywhere other than a vocabulary and classification for Attribution. But I see light; an inkling that actually there may be value and progress through this analysis …
After all of which you deserve:

[Grand hall of the burghers. I.e., the 0,1% …; Brugge again]
OK, herewith Part IV of:
Tinkering with some research that came out recently, and sometime(s) earlier, I had the idea that qua fraud, or rather ‘Cyber’threat analysis (#ditchcyber!), some development of models was warranted, as the discourse is dispersing into desparately disparate ways.
The usual picture suspect:

[Mock defense, open for business at Brugge]
Second up, as said: The same matrix of actor threats, (actor) defenders, but this time not with the success chances or typifications or (read horizontally) the motivations, or typical strategy-level attack vectors, but basic, strategy-level defense modes. Not too much detail, no, but that would not be possible or the matrix would get clogged with all the great many tactical approaches. Those, laterrrrr…
Next up (probably the 16th) will be a discussion of movements through the matrix, matrices (by taking both the blue and the red pill; who didn’t see that option ..?), for state actor levels. And (probably the 18th) a somewhat more in-depth view on the above matrix.
Hmmm, still not sure this all will lead anywhere other than a vocabulary and classification for Attribution (as in this piece). But I see light; an inkling that actually there may be value and progress through this analysis …
OK, herewith Part III of:
Tinkering with some research that came out recently, and sometime(s) earlier, I had the idea that qua fraud, or rather ‘Cyber’threat analysis (#ditchcyber!), some development of models was warranted, as the discourse is dispersing into desparately disparate ways.
The usual picture suspect:

[What no throwback to the socialisixties ..?]
Second up, as said: The same matrix of actor threats, (actor) defenders, but this time not with the success chances or typifications or (read horizontally) the motivations, but with typical strategy-level attack vectors. Not too much detail, no, but that would not be possible or the matrix would get clogged with all the great many tactical approaches (including social engineering, spear phishing, etc.etc.).

Next up (probably the 12th) will be typical countermeasure classes.
Hmmm, still not sure this all will lead anywhere other than a vocabulary and classification for Attribution (as in this piece). But I see light; an inkling that actually there may be value and progress through this analysis …
Earlier we wrote about how the self-driving cars till now, weren’t. Were more like ‘world-map programmed in, some (humanity oh dear how irrational) noise added’-navigating cars.
Now, we’ve entered new games, like the Big G possibly taking on Uber through employing self-driving cars – which would make the shrill reality of jobless growth, as predicted for the taxi industry a reality; where do all the taxi drivers go ..? And suddenly, there’s a new entrant on the other front. This one might pear fruit. If, big if, they’ve tackled the hard AI problems XOR they’re on the same lame track. [As said, the essence in this earlier post]
Or it’s just an as yet unheard of thingy for a new round of Connected Car developments. Or…
And then there’s dark horses lurking in the background. Like Tesla (/ Hyperloop?), and others you have no idea about yet.
OK, speculation, speculation, … Just wanted to note that there seems to be movement on the AI front leaking into the Real World. Or not. But there’s things a-brewin’.

[Cloudy weather, dark picture. Still, let’s pray for progress ? at Colline du Haute]
With DARPA’s quest for Active Authentication (as here), what will the future spread of (non-)repudiation look like ..? By means of strength of proof e.g. before courts, when system abusers may claim to accidentally have the same behavioural ICT use patterns as the unknown culprits, or be victims of replay attacks.
I’m unsure about how this will play out, then; whether Innocent Until, or Proof of Innocence, or even Reasonable Suspicion may still exist.
Yeah, I get it – you’ll claim that this is for DoD purposes only. Of course, as it never has, in the past. @SwiftOnSecurity would (need to) be on the alert.
Well, as this kind of innovation (by this agency) usually reaches society in all sorts of very unexpected ways, there’s hope that something in support of the Constitution may in the end come out… for now, I’ll leave you with:

[Light on the inside, though without outlook… FLlW at Racine, WI]
The spectre of BCM has been haunting ‘business’ departments of about any organization for too long. It needs to go away – as spectre, and take its rightful place in ‘Risk’ ‘Management’. The latter, in quotes, since this, this, this, this, and this and this.
Much link, very tire. Hence,

[Opera! Opera! Cala at Vale]
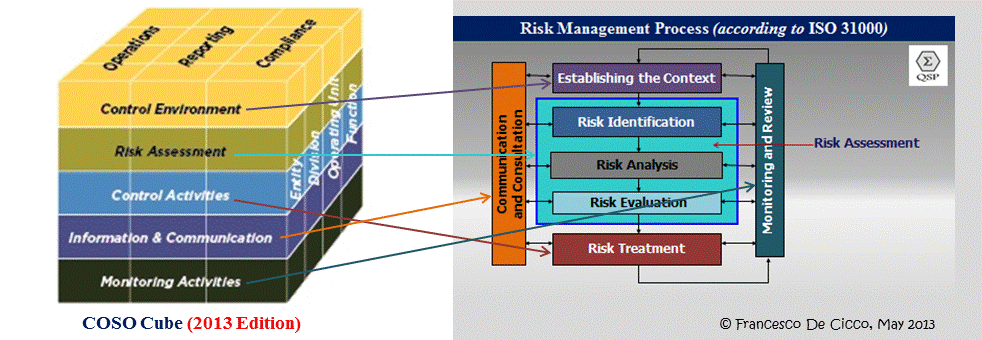
Which actually brings me to the core message: ‘Governance’ [for the quotes, see the last of the above link series again] fails for a fact (past, current, future) if it doesn’t include risk management, and when that doesn’t take this into account:
[Here, highlighted for InfoSec as that’s in my trade portfolio…]
First, a reference to that RM-in-Gov’ce mumbo jumbo: Here. (In Dutch, by way of crypto-defeating measure vis-à-vis TLAs… (?)) Listing among others (diversity, sustainable enterprise, external auditor role) the need to do more about risk management at ‘governance’ levels. Which might of course be true, and how long overdue after COSO has been issued and has been revised over and over again already.
But then, implementation … No strategic plan survives first contact with the enemy (ref here). And then, on turf are the wars that be, in all organisations. Among the great multitude of front lines, the one between Information Risk (management) the Light brigade [of which the Charge wasn’t stupid! It almost succeeded but because the commander wasn’t a toff so supporting a brilliant move by such an upstart wasn’t fashionable, he was blamed – an important life lesson…], being overall generic CIA with letting A slip too easily on the one hand, and the all too often almost Zero Business Continuity (management) on the other, outs the lack of neutral overlordship over these viceroys by wise (sic) understanding of risk management at the highest organizational levels. As in the picture: It’s all RM in one way or another. And (though the pic has an InfoSec focus) it’s not only about ICT, it’s about People as well. As we have duly dissed the ‘Process’ thinghy as unworthy hot air in a great many previous posts.
Where’s this going …? I don’t know. Just wanted to say that the IR-to-BC border is shifting, as IR becomes such an overwhelming issue that even the drinks at Davos were spoilt over concerns re this (as clearly, here). But still, BC isn’t taken as the integral part of Be Prepared that any business leader, entrepreneur or ‘executive’ (almost as dismal as ‘manager’) should have in daily (…) training schedules. Apart from the Boy Cried Wolf and overly shrill voices now heard, the groundswell is (to be taken! also) serious: IR will drive much of BC, it’s just that, again, sigh, the B will be too brainless to understand the C concerns. Leaving BC separate and unimplemented (fully XOR not!) next to great ICT Continuity.
Or will they, for once, cooperate and cover the vast no-man’s land ..? Hope to hear your success stories.

Voor sigaren bepalen we het profiel aan de hand van de criteria Smaak, Balans, Body, Sterkte, Aroma en Finish.
Voor Smaak pakken we het aromawiel erbij. Let wel I; wat u proeft of verwacht, kan gedurende de diverse fasen van het roken nog variëren... En let wel II; er zijn ook aspecten die nog niet zozeer als aroma staan aangegeven in het wiel, we denken aan termen als (ja de sigarenwereld is langzamerhand, helaashelaas US-, Engels geworden) zesty, tangy, floral, en earthy, of soms zelfs metallic. Lijkende termen die een combi zouden kunnen zijn van diverse aromas en papillaire en olfactorische/nasale sensaties en -tactiele invloeden. Hierbij komen termen als 'complex' uiteraard ook bijgepakt, om in dit geval te beschrijven dat er vele aromas herkenbaar zijn. Rustig roken, dat is niet alleen beschaafder en allerlei sigarenrokeneffecten-versterkend maar biedt ook meer kans om aromas te onderscheiden.
Balans is voor de hand liggend; of de zoete, zure, zoute en bittere tonen (OK, en 'umami'...) in balans zijn. Ja, ook bij een sigaar – al zal het meestal gaan over de balans tussen 'creamy' en 'spicy' en gaat het meestal mis door te veel bitter of te veel spiciness.
Body gaat over de volheid, in dit geval vooral te bepalen aan de volheid, dikte, dichtheid van de rook. Die ook een gevoel geeft; 'light' is als een licht bier, 'full-bodied' is als een rechttoe-rechtaan whisky of cognac.
Overigens hoort bij Body ook textuur, 'leathery', 'meaty', 'silky', 'creamy', 'soft', 'succulent', 'woody', 'chalky', 'dry', 'oily' en 'spicy'. Die dus net niet hetzelfde zijn als de aroma-indicatoren uit het wiel; soms overlappend. Niet handig maar zo is het nu eenmaal.
Sterkte is een wat eenvoudiger maat voor het nicotinegehalte van de sigaar. De topbladeren van een tabaksplant heeft meer nicotine dan de lagere bladeren – me(n) dunkt dat de topbladeren zijn waar de plant verder wil groeien en dus betere bescherming nodig heeft van de nico; lager is het wat ouder en 'expendible' dus ga je daar als plant niet je nico op concentreren ..? Waar de sigaar van gemaakt is, heeft dus invloed. Kan je meestal niet kiezen, maar wel proeven. Rustig roken is ook hier handig; om een nico-klap/duizel te voorkomen bij het opstaan.
Aroma dan, vervolgens. Ook hier kan het aromawiel worden ingezet. Vreemd genoeg is het moeilijk de aromas te bepalen als we zelf roken; iemand anders' rook kunnen we beter analyseren. Of we blazen de rook door de neus uit ('retrohaleren'), dan hebben we wel de volle verfijning (ga ik vanuit, lezer!) van onze neus ter beschikking. Bedenk bij het 'benoemen' overigens dat we veel meer uit ons geheugen putten, qua eten en drinken!, dan we wellicht zelf(s) denken. Dus rare smaken herkennen is niet raar.
De Finish ten slotte is kort of lang, naargelang de aromas lang op de tong (sic) blijven hangen. Milde sigaren zijn nogal eens kort – hetgeen niks zegt over de complexiteit, overigens. Hierin zit ook de reden om een zwaar (sterkte)kanon na een milde te nemen, niet andersom.
Als het gaat over de champagnes en hun profielen, pakken we er de (echte en semi-)klassieke wijn-analyses bij die we allemaal wel kennen; onderscheidend in [Hier verder. In ieder geval https://www.wijnwinewein.nl/hoe-proef-je-wijn/ en aromawiel + zuurgraad/tannines/body(viscositeit/alcohol/tannines/smaakintensiteit/mondgevoel)/afdronk + Aanzet/Zuren/Zachtheid/Tannine/Body en alcohol/Afdronk/Smaken dus de aromas bijna-los van structurele criteria. Dan de smaken matchen met die van sigaren, of niet; Klosse's overlap/contrasten erbij halen en dan verder. En toespitsen op champagnes... pak het smaak-plaatje van het CIVC erbij!]
Dear reader; bij deze dus de waarschuwing dat u vanaf hier (?, inderdaad, echt niet alleen hier) serieus te lange zinnen tegenkomt.
Ach, daar ben ik me prima van bewust, mijn hele blog is immers ook een poging tot schrijfoefening in alle facetten. Sommige posts daar blinken uit door korte zinnen en ellipsis; ook deze pagina is opgesteld als tegenwicht. En ik vertrouw erop dat u dat gewoon doorlezend aankunt.
Als voorbeeld: Oplettende lezers zullen opmerken dat onderstaande waar het uitweidingen achter links naar andere pagina's betreft wellicht beter met behulp van OnMouseOver's, alt-tekstblokken of andere tags per pop-uppable item zou kunnen zijn geïmplementeerd maar ik heb het zo gekozen en ik kan best komma's toevoegen in deze zin maar ook dat heb ik achterwege gelaten zonder de leesbaarheid of de begrijpbaarheid in het gedrang te brengen.


Inderdaad, het ontwikkelde, ik schreef, een en ander vanuit een voortdurende, voortgaande research. Na zoeken in het wilde weg algemeen, navraag bij het Comité (iv) Champagne, een aanvullend zelfzoeken met Google Satellite én Street View zowel rond de officiële als in het algemeen, kwam ik tot de Lijst Van (uiteindelijk) 84. De en passant gevonden kaarten leidden tot enige aanvulling. Toen kwam ik Weinlagen.de tegen en tsja dan ben ik niet meer te houden qua sys-te-matisch alle streken én plaatsjes af! Hoewel, ... in onderstaande tabel heb ik maar niet meer voor ieder stuks de Street View erop losgelaten of onderstaand ingevuld. Terwijl ik er vanuit ga dat dit alles nog aanvulling kan krijgen ... Les Clos Inconnus zijn uiteraard zichzelf.
De gangen kwamen al zeer onregelmatig door, en met andere tafels die uitliepen en/of (weer) bijtrokken, tot zeer ver inhalen zelfs, tot gang 6 van de 7 tachtig (schrijve: 80) minuten op zich liet wachten, ondanks diverse malen navraag. Waarna het nauwelijks-opgewarmde pompoen met koude polenta bleek te zijn; "dat hoort zo" ammehoela. Nee, het niet-koude nagerecht erna hebben we niet gehaald; we zijn opgestaan en weggegaan. Die zien ons nooit meer, zeker omdat de bediening ook Zwak was (gangen aan verkeerde tafeltjes serveren want die waren al twee gangen verder), etc. En balsimaco-saus dus, 'et al.'...
Huh, da's écht voor de Insiders..? Inmiddels wel toegestaan als aanplant, maar nog zo'n drie tot tien jaar onderweg voor er de eerste re-de-lijke wijnen van kunnen worden gemaakt en dan is het nog maar afwachten. Je weet het niet van tevoren hè, met zo'n non-Vinifera druivensoort..! En dan had je Floreal, Artaban en Vidoc nog niet gezien. Die mogen (in de toekomst) ook... En dan is het Comité Champagne ook nog bezig met kruisingen van de Top 3, Arbane, Meslier, en Gouais. #feest
En dan komt hierna een nóg spectaculairdere outsider: Chardonnay rose Rs, minder dan een kwart voetbalveldje aanplant...
Mineraliteit verdient een aparte behandeling; vanuit het idee van 'huh er zit echt geen mineraal/steen in je wijn en lik jij aan stenen-dan'-versus-'toch proef ik die sensatie en Ja' tot en met de abstracte benadering van een kennelijke associatie van een gewaarwording als hier, tot een synthese op de as 'bodem-microbiologie'-in-combinatie-met-'feitelijke chemie'. Want, jawel, fenylmethaanthiol zorgt voor vuursteen / aangestoken lucifer, in combinatie met benzaldehyde (uit 'hout') en waterstofdisulfide (uit reductie; en beide uit bepaalde gisten!) leidend tot Vuursteen-herkenning, versterkt bij anorganische ammonia bijvoorbeeld. Vuursteen is geen 'mineraliteit' maar daar wel belangrijk onderdeel van. Dus Ja, er zitten wel degelijk chemische stoffen in (niet alle gelukkig) wijn die een sensatie veroorzaken die op mineraliteit lijkt. Zout, uiteraard, ook, (niet meer maar wel) vaker dan we denken! Alles tezamen een uit-ste-ken-de reden om te spreken over herkenning van Mineraliteit in wijn. 0-10 en een penalty tegen voor de geo-logen.
Laherte Petit Meslier in the tasting round
Yes @laherteaurelien makes a monocépage of this one. Great Meslier it is:
The golden colour would suggest something dosée, but look closer and you notice a hue which points to slight bitter influences. And indeed, on the nose we get a whiff of smoke, certainly straight after the pour; quite an opportunity to use the word ‘empyreumatic’... Did I mention Meslier already? One to one it is. But nothing referring to your cooking qualities; it’s more like a distant secondhand puff of Belinda – I’d not suggest you buy that for comparison; trust me as smoker it’s trash but as Meslier aroma it’s excellent full stop. Crispy dry cigar smoke fits better.
Certainly, since this all is followed up, much more persistently, with quite some mature lemon and a whole slew of herbs and spices notes. It smells like a merry-go-round of eucalyptus, dill, thyme, spearmint, soft mint, basil, anison, verveine... wormwood even; those that know génépi, find it here, too.
The first sip jumps in with a most delicate mousse, a sensible but not too fatty mouthfeel, nicely balanced with lemon dominant in combo, and ginger/pineapple/mirabelle and dry lemon rind flipping back and forth. In the remarkably long finish, the rind does a gentle cleanse.
But I couldn’t find any cardamom that some mention, nor cocoa or coffee. All in all, in cocktail terms it would fit in the range of the French 75 and a Fleurette.
I’ve tried a little bite of camembert, but you shouldn’t. The bitter of the wine is lost but notches up in the cheese, which tastes odd. The fit with lightly aged Comté or same-Gouda is perfect, however. Sushi should work, too, if with a suitably subtle pinch of wasabi, no more – harsh coriander, algae, chervil, wasabi as such weren’t in the nose.
In summary: All of you should have a taste of this one, or one couldn’t be trusted on champagne connoisseurship.
[Degorge 12-2021, hence the progressed maturity]
Links:
https://maverisk.nl/de-forgotten-four/ for Petit Meslier
https://maverisk.nl/champ-sigaar/ on the cigar smoke angle
https://maverisk.nl/geneprima-spul-hoor/ on génépi
https://maverisk.nl/mirabelle-wil-iedereen-welle/ on mirabelle
@champagnepascalmazet make quite an interesting range of wines, fully certified bio since 1980. We tasted the Cuvée Originel bottling of 2014, for its 35% Pinot Blanc of course; interested to learn how such a Forgotten Four lead, with the three Usual Suspects trailing, would work out.
‘Splendidly’ is the answer.
The gold is striking, the nose is suitably complex. One gets mint, cucumber, cornichon tartness (I mean, the true kind of https://www.kesbeke.nl/) and some olive.
On the palate, it switches to agrumes-allsorts. Yuzu, lightly pre-ripened apricot (yes there’s acidity in there), sparkling grape (ah.) and a hint of almond already. This slowly develops into lemon-grapefruit on the one hand, and yellow curry / pineapple on the other, with a tangerine almost orange'y element integrating both sides. I’d say, there’s a marbling of mirabelle (in Dutch: https://maverisk.nl/mirabelle-wil-iedereen-welle/) running through it as well.
‘But’ overall it certainly is far from flubby (the 3g dosage having turned into the above, no sirup) or acidic. The quality of it all, and the light oak touch, twist all the richness back towards the freshness of citrus zest. And did I mention the mousse is still there, slowly releasing?
Towards the lingering finish, this all persists in a extremely well-balanced acidity and a hint of minerality and sophisticated bitterness.
Am I happy to have another one of these standing ready
Marie Courtin Présence
I bought the @ch_mariecourtin for the 1/3 Pinot Blanc (of course: https://tinyurl.com/ForgotFour !). High expectations, exceeded.
First off, the yellow-golden almost amber colour would promise some sweet almost creamy elements. But with a delightfully tingle from a fresh mousse, and a light bitter-tartness in the nose, the picture turns around completely. There’s Mirabelle ..! [As per: https://tinyurl.com/Mirabellepg]
The palate is perfect; not too much mousse so the real ‘wine’ taste is clear, and the Mirabelle keeps on coming. The mouth feel overall is well-balanced, and includes a soft minty/dill side with the lemon (plus some bittersweet orange even), moving into the grapefruit area and then the mirabelle’s back again. The very long finish has the mint/dill combo again, and an inkling of sugar. But with zero dosage, that’ll be the Chard and almost certainly the Pinot Blanc waving goodbye. Throughout, there’s a slight undertow of pickled cornichon (Amsterdam style; what else?)
All in all, it’s a wonderful demo of what Pinot Blanc can bring; lifting the Chard from its average whilst pulling itself up into high performance. Merging the best of both into Something Else of a great wine. This being a zero dosage, zero sulphur added, zero intervention wine, it also proves that ‘natural’ wines need not be f(l)unky. But on the contrary, one would hardly be able to tell.
The Présence is course material in so many ways. Am I happy? Well, not with six other dwarfs but yes, very much so.
The @champagne_gruet Cuvée Arbane …
𝘚𝘰𝘮𝘦𝘵𝘩𝘪𝘯𝘨 𝘌𝘭𝘴𝘦 entirely!
100% Arbane yes. Which brings a freshness too long lost. Reminds me of the bone dry styles of yesteryear, in a good, rather great way. Chalky without dust, minerality without flint. A wonderful conversation starter, on the good things of life.
With a fresh and quite light, lemon-white colour through which a very fine and persistent mousse promises delight. Then, on the nose, one gets a first whiff of floral notes; jasmine, elderberry, rose – followed by zingy but ripe lemon. When allowed to mellow in the glass (or a day in the bottle), the lemon slowly brings along some grapefruit, pineapple and (dry white) melon. All within measure, refined, nowhere too in-your-face’y.
The mouthfeel is brilliant with the mousse playing its role to keep the very well balanced aspects all quite light. The dosage is hardly noticeable – from the taste of it, one would estimate 2g. max, and notes of soft white peach, light albedo, with a very long finish on the thyme/mint/dill spectrum with the albedo bitters lingering on.
Would work miraculously with e.g., flounder with serious sauce and herbs, swordfish with almond crusting, maybe tuna or mackerel, or white meat.
Saw a score somewhere of 91/100, but that's too low.
Buxeuil doesn’t have any Arbane of its own (in production), but with this Gruet wine, it has a flagship.
Arbane being at only 0,018% (yes, percent) of Champagne’s acreage, this cuvée highlights the 'need' (want!) for quite an extension of that.
Tasting the Pinot Blanc champagne of Gruet of Buxeuil (@champagne_gruet). That’s right, a pure-bred PB champagne. (Be sure to pick the right one, at https://www.champagne-gruet.com/)
And it is a treat, indeed.
In the glass, we have a very fine mousse, well-integrated - it continues very, very long and doesn’t just give a one-off foam layer – through a pale gold, slightly varietal-typical PB wine.
On the nose, the typical character come through immediately, including a slightly fluffy air of white flowers around light tangerine / (white) peach / mirabelle, and a core of lime – keeping nicely short of being bitter.
The mouthfeel is light, but not fleeting. One gets beautiful straight near-ripe lemon, a waft of mint with white blossom, and some white pepper towards the back. Add to that lemon white skin with edges of red grapefruit.
Mind you; I had kept some for a second tasting, and four days (suitably cool storage) after opening, all this was still as fresh. No ‘dosage plays up after too much air’ or so; great.
A top recommendation, this one. If only to keep the Forgotten Four Cépages alive, as they deserve, but also for sheer tasting pleasure. Or ‘the trick one’ at a tasting experiment. Or for an apéritif or with whitish seafood (if not to lime’y or salty).
The Réminiscence 100% pinot blanc brut nature by @champagneericlegrand via @jeromeschampagne. Supposedly off 65+yr old vines, but one would be hard-pressed to tell that by the wine. What delicious freshness!
For a start: What would one expect from a pure PB champagne? Subtlety indeed.
It starts with a new capsule (for me, to further fill my https://www.deknudtframes.fr/en/catalog/product/s65sz2-/frame-in-black-for-champagne-caps which only applies to *different* capsules I tasted *at home*) – under a muselet to duly impress. After a good whiff, one can immediately pick up the something-different of this one. The first 80% is most clearly artichoke with some mint; not very strange since we just made such a dip for (neutral) crackers five minutes before.
After which, with careful nosing/tasting, we get a white-floral element with traces of almonds and yes even a hint of vanilla and the slightest of dried yellow fruit. This continues in the long developing taste, clearly adding ‘a point’+ ripe lemon (citron), with the etheric element slowly (very slowly) fizzling out. Can I say ‘retronasally’ there? As it tactilely *feels* that way for sure. Add some vanilla points in the long after.
All in all, a thing to be savoured. And, let’s promote these ‘forgotten four’ champagnes! Away with the factory work! (One suspects the 24x range by some famous grand marque points in the right away direction, too, qua hyper-mass production orientation.) The more sure we have of being able to choose to never have to taste a same champagne ever again in one’s lifetime. *If* one would want to – wines like the Réminiscence make one still would want to return often. Extend the plantation!
Another round for Gruet of Buxeuil (@champagne_gruet) – The Cuvée des 3 Blancs (as here)
With its matte gold, almost amber appearance and very fine mousse (hardly foamy but lingering in the mouth for a long, long time), we'd expect the Pinot Blanc to dominate over the Arbane and even Chard. It does. A little. But, as assemblages go, only a little; I'd rather say one can identify the PB by its gently soft but full agrumes/mirabelle character but there's a lot of exquisite light flowers – hawthorn – and herb'iness – in the sage, rosemary corner – already in the aromas. Would that be the continuum of the Arbane and Chard?
If one would want to take it analytically.
Savouring, one would enjoy the all-round calm structure, with a medium to full mouthfeel (nothing sticky). And just the image (?) of a surprisingly light white wine with lots of mature grapefruit, lemon and a slice of lime. From which the little bitter note lingers on in the back, most pleasantly refreshing, nothing astringent or harsh. Overall, certainly not chalky bone dry but a hint of mango.
Would I pair this all with food ..? That would be a. hard; a very careful cheese selection might do, b. interesting, to see where the flavours go (see below), c. not necessary, it's a wonderful treat on its own.
This, in a series of Forgotten Four tastings, as per this 'research'.
And the (aubépine and) mirabelle note, Gruet themselves also list. Nice, yet another example of that great aroma.
Plus, one of course has e.g., this and this book, or quite a few others, already..?
Of boek. Hoewel er een beperkt aantal boeken is dat ik hoog heb, zit er niet een[1] bij die nou net op het onderdeel dat mij respectievelijk interesseert, het α tot en met ω heeft. Waar-om en waardoor ik juist de verdere research wil/ 'moet' doen...
[1] Nou ja, deze komt in de buurt...
Jazeker! Zoveel is zeker: Voor bijvoorbeeld de Fransen is dat een volstrekt normale karakterisering. Het gaat dus niet om NaCl uit een Jozo-vaatje... Eerder "off-vuursteen"; denk ook aan de regio van hints in de verte bij wit-peperigheid en magnesium in de buurt. Niet vreemd, als oesters zeer rijk zijn aan zink (sic), ijzer, calcium (dûh) en selenium. Sommigen in NL zeggen dan dat je geen 'zout' of zelfs maar 'zilt' mag zeggen. 1. Van wie niet ..!? 2. Waarom niet ..!? 3. Dat is toch voor zéér velen de beste karakterisering – niemand beweert dus dat er keukenzout in uw wijn zit en iedereen weten dat de karakterisering losstaat van enige bewering van objectieve chemische samenstelling anders zouden we wijnaroma's héél anders beschrijven!
Of zelfs Philpatrick het moet niet gekker worden ... Dus denk niet dat de spellcheck op hol sloeg.
De Cuvée Métisse, noirs et blancs oftewel 80% PN en, jawel, 20% Pinot Blanc, wederom een assemblage met een van de Forgotten Four. Brut nature dat houdt het puur, klaargemaakt bij de BV Val du Clos dan nemen we ook een verre hint daarvan mee. Van Champagne Olivier Horiot, MeB juli 2020, dégorge 16 jan 2023, grotendeels oogst 2019 plus nog een scheut uit de Réserve Perpétuelle die op eik wordt gehouden – ja ik kwam 'm in een coin oublié tegen maar prijs me gelukkig. Quelle belle ouvrage! Als u denkt: Da's een nogal technisch verhaal – dan is dat juist maar het proeven is gewoon een onbekommerd plezier. Het begint uiteraard met de sprankelende licht-amber kleur en een neus met het lichte bittertje, denk aan het dille-thijm spectrum, van de Blanc. Terwijl dan de eerste smaak van de Noir komt. Hoewel licht door de jaren, en dat pufje bitter komt er snel weer bij. Rijpe-appelzuur, heel lang gematigd door-coastend verdund citroensap met in de verte mango en met witte zest erboven zwevend. Maar wel in complete balans, niet vlak of zo maar juist met transparante diepte. Toen ik er een hapje net-nog-niet-compleet-rijpe ananas(kern) bij nam, was dat een moeiteloze, zowat volledige overlap. Later komt er een onderstroom(pje) van iets dat neigt naar kruiden door de mond. En nog steeds met zeer fijne bulles, by the way; verfrissend zonder prikje. In termen van verwachte aroma's zou ik eerder tussen Chard en Meunier op pad gaan van jong naar iets voorbij het midden, en zeker niet te ver naar de rijpe complexe PN-hoek zakken. Al met al een 'opulente' wijn die verrassend jong van geest is (gebleven). De PN is meer steun dan leider in het geheel; prima! En de PB viert z'n vrijheid om te shinen; uitstekende reclame!
5 Sens: De Oogst-2017, MiB 24 juli 2018, Dégorge 12 mei 2023 ja zo exact, met nul dosage voor slechts 1320 fles plus 90 magnums. Van 5 verschillende terroirs, oude stokken van 5 verschillende cépages – PN, Chard en Meuier, en dus ook Arbane en Pinot Blanc; langzaam vergist en opvoeding sur lies. Dat geeft volgens de makers de vijf (jawel) elementen Water, Aarde, Luchten Vuur – en l'Esprit! Wederom een assemblage dus van Olivier Horiot (op @horiotolivier) met Forgotten Four, klaargemaakt bij de BV Val du Clos dan nemen we ook een verre hint daarvan mee. Zo, dan heeft u de data gehad. In termen van aroma's als op de vaste plaat gaat het alle kanten heen, waarbij we ook (laten we zeggen 'traditionele') Chard- en PN-aroma's tegenkomen. Maar niet te uitdrukkelijk. Om het op een rijtje te zetten: De kleur is vol maar licht goud; De mousse is heerlijk, (nog) ruimschoots aanwezig maar zeer fijn; In de neus krijgen we eerst rozenblaadjes en een tikkie mango, maar zo nu en dan ook een zweem ziltigheid ..? Een ander zou het ook witte-peperigheid kunnen noemen. Sommigen vinden dat Arbane meidoorn en anjer geeft; nou ja dat kan ik begrijpen maar pikte ik niet op. Noch wat appel en kweepeer, dat gewicht trof ik minder: Het volle mondgevoel zit stevig in de citrus-hoek. Denk aan lauwwarme, (over)rijpe citroen met een beetje suikerrijpe peer en (geblancheerde) ananas, op het mirabelle af maar wel met een los zwevend zuurtje dat eronderdoorlangs komt zweven, inclusief een puntje venkel/dille. Ik denk dat hier vooral de wat rijpere Pinot Blanc om de hoek komt kijken. Maar al met al wordt het nergens te zwaar; de wijn blijft gewoon helemaal in balans; De citroen is de core der (talrijke) caudalies; zelfbewust maar niet zwaar. Nou ja, als eindconclusie; deze zit op het niveau van een lichte montbazillac of sauternes met mousse..! Werkelijk heerlijk. Voor zover er wat bij moet worden gehapt, zou ik zeggen: Niet te licht, niet te dicht op de sla/Brillat-Savarin-hoek, of te kale zilte oesters. Eerder oesters met enige bewerking, zou ik zeggen. Als per deze – en een geel- of roodschimmelkaasje kan ook nog prima. (vandaar; lichte sauternes ...) – oh en een salade met cajunkip kan ook ...

Étoiles du Nord, voor uw betere wijnen...
Al is het alleen maar door Il Respiro del Vino te kunnen lezen; geen vertaling tot nu toe dan maar zwoegen.
Le Chardonnay rose est une mutation du Chardonnay blanc que l’on trouve historiquement à l'état de ceps isolés dans les vignobles champenois et bourguignons. La mutation porte principalement sur la couleur de la baie qui est d’un rose foncé à maturité. Cette différence a abouti à la proposition d’individualiser le Chardonnay rose comme une variété distincte de sa forme blanche et de l’inscrire en tant que telle au Catalogue français.

L’origine de ce cépage est difficile à dater. Néanmoins, il existe quelques repères comme la date de son introduction dans la collection de Vassal-Montpellier en 1950 ; deux accessions (ou "introduction" est un clone non agréé conservé dans une collection) de Chardonnay rose y ont été plantées cette année-là. La première, issue de l'ancienne collection dite "de Ravaz" de l'Ecole de Montpellier (donc la date réelle est antérieure à 1950), provenait initialement de la Côte d'Or. La deuxième provenait de la "collection Couvreur Pernin", à Rilly-la-Montagne dans la Marne.
Depuis peu, le Domaine de Vassal-Montpellier possède également deux accessions assainies issues du clone de Rilly-la-Montagne. Récemment de nouvelles accessions de Chardonnay rose ont été recensées dans le vignoble champenois, preuve d’un intérêt croissant pour ce cépage ancien. Cependant, la disparition progressive des veilles vignes ainsi que la pression croissante des viroses, faisaient craindre la perte de diversité génétique au sein de ce cépage et l’abandon de sa culture.