Once again, there you are. Because Monday:

Tag: domotics
Deinduction
OK. To be, think, human, two things seem to be required:
No, not the dichotomy of deduction versus induction. Not so literally (literally, I mean like owemygawd). But the top-to-ground-then-back-up-again ‘logical’ goal-directed problem-solving reasoning, versus the speculative wandering of the mind. Perspiration, and Inspiration. Taking correlation for causation, versus fuzzy-logic supported hypothesizing. OK, I admit I threw in the fuzzy logic part to confuse, and to discombobulate your comprehension.
But still, therein lies the foundation of Theories, the brickwork of thinking: Is there a priori knowledge, or is everything we know only valid within its own framework of reference..? Is the definition of definition circular or not, or in some circle..? Should, must be, to be basis for theory-building.
Expanded upward by Kuhn and Lakatos, drilled down by a great many, philosophers mostly — that haven’t delivered workable answers yet. Not workable at least, to span the gap in between neurobiology and psychology. Which is where AI-as-we-know-it will have its place, after which it will be vastly expanded to cover it all. Maybe not individually embodied, but will.
And, there’s no either/or. There’s the spectrum ..!!
And all this, relevant for the grounding (both ways, please) of ‘Big Data’. Think that one through!
C’est arrivé près de chez vous; LoRaWAN
Yet another major building block of the Future … in place. [And, not a ref to some City of Light atrocities]
Where’s the Privacy and (OR) Security experts …? For certainly, though almost out of public view, the undercurrents develop fast, into a maelstrom — I’d like it even more in this form — of possibilities; to be abused before being controlled, as has always been the case throughout history.
Oh well, can’t stop Progress, certainly not of the Technology kind… But one can hope we (sic or huh?) the Concerned will be in sufficient numbers to be able to and to be allowed to insert the appropriate controls into the whole shazam.
Like, you know,

[Or is this an Tocqueville’ian opposite ..?]
Privacy for drones, *from
Some found it odd that e.g., in Chicago, the ground floor space, the up into the air (no not that) building, and the naming rights to that building, are traded separately.
Elsewhere, one’s home comes with an expectance of Privacy, “behind one’s front door”. But not outside; that’s free game for any … usually still ..!, photographer when from public space.
But now, back gardens, previously considered safe from prying eyes, are visible from other, 3D public space: the air. Via drones.
Which takes care of the public space part, where the ‘photographer’ (?) still is without even the need to trespass ’cause the camera is unconnected to him (sic). [Apart from the argument that just about any official could claim access to the back yard as if semi-public space..?] But does it nullify the “shouldn’t have been outside” argument ..? Or is the previously invisible part of the garden also part of the interior..? As it had similar/same protection by having needed illegal means of access hence the expectance of privacy — that now, by the legality of that access not having been arranged (yet), is still in doubt and the morons “break in” regardless.
Hence the start with the above distinction: Would the air over one’s house be private property as well (How high ..? At least till levels of commercial flight, that is regulated), then possibly, flying a drone into it would be trespassing. But immediately, since camera resolutions increase so quickly, we would need protection against prying eyes from above the streets as well, looking over rooftops. Hm, we would revert to the “expectance of privacy” argument back again anyway. And the automatic ownership non-transfer would prevent shooting them down, still.
So, hopefully, I’ve made you think. Else, there’s no result … ;-[
Oh well:

[Beauty exposing herself very publicly… above not under some n.rds? Voorburg]
Where are VR, its breakthroughs ..?
Dropping another question for your tons of response … haha.
Wondered why VR hasn’t broken through to ubiquity. What’s holding it back? I mean, I understand that it’s quite complex, not just an app to be installed and there’s all sorts of physical constraints and installations to be made as portable as possible — but still, hasn’t the invention been around long enough for some, Tesla- or Watson-like breakthrough to would have been able to surface ..?
First next one through the gate, can make a fortune. Leaping over the current offerings, that have so diligently explored all details? Or is it just that there already is enough reality to still be explored with all the senses, out there? That would explain how annual airline mileage still grows so much despite the explosion of touristically oriented vlogs let alone Youtupe channels that were said to replace so much travel.
[Edited to add before publication: Oh yes there’s some chatter lately about VR but that’s mostly about brain warping and rather fundamental still — corroborating my point.]
Oh well. This:

[Get off your fat a’s, or travel by fat a boat — that’s a plane in the water.]
Oh, whatev’ – will succeed
Yes, critique hasn’t been overly enthousiastic for the HoloLens developments. Like in this here story.
Question is, though: Did the first iPod have Shuffle? Was the first iPhone even a serious phone ..? [Or was that the first iPad that had no comms; I forget due to irrelevance. But do notice how there’s now a continuum of screen sizes from smartphone via note and tablet to desktop screenlets and mega-TVs]
My take: It’ll be somewhere on the Glass–to–iPad scale: As prototype that stays (sic! Glass’s still around for very, very effective deployment in some sectors) and/or as lauch of a steep improvement curve.
Which is good. But may bring about some unforeseen consequences: What when Youth gets hooked, and unlearns what Reality is ..? Will we all follow ..?
Yes, if e.g., walls can be presented hologrammatically to a degree that hologrammar-Ns (you read that here, first!) are satisfied with reality resemblence, could an ASI take over and confine us in virtual (now for realz) boxes ..?
Dysto here, dysto there, dysto everywhere… Hence:

[Mockery … Barça]
Mundane chores
SwDIoT
Recently, there was yet another exepelainificationing of ‘software defined networking’, along the lines of separation of the control plane from the data/content plane (here).
Which ties into a core problem, with IoT the subject of this post: Integrity.
Yes, confidentiality may be an issue, but singular raw data points themselves often are too granular to actually steal any information from. And Availability is of course also of the essence, especially in ‘critical’ systems. But te main point of concern is with Integrity, of the system in a wider sense, but also in the smallest sense.
Take Stux … Integrity breach as the vector space, spanned along a great number of dimensions.
Objective: Degradation of the information value; increasing the variance to a level where noise overwhelms the R2 of the signal (however far from log2(n), big if you understand), through degradation of the (well, original) software integrity.
Path: Introduction of intentionally-faulty (?) software. With use of of, probably, penny-wise correct IAM, being pound-foolish at the medium level. I mean, the level where human and other actors are unwitting accomplices in planting da bomb. That’s what you get by simpleton top-down compliance with just about every thinkable rule: To do any work, underlings will devise ways to circumvent them. And, adversaries will find, see, avenues (that wide) for riding on the backs of the faithfully compliant to still achieve the objective.
But OK, back to … separating the control plane from the data plane. Bringing a shift in efforts to disrupt (no, not of the mehhhh!! destructive, economy-impoverishing kind but in the actual signal degradation kind) from just-about any attack plane down to, mostly, the control plane. That may seem like an improvement, de-messing the picture. But it also means shifting from a general, overall view of vulnerabilities to the core, and a core which is less tested or understood, and harder to monitor and correct, than previously. Or is it ..?
So, if we take this Software Defined to IoT, we’ll have to be careful, very careful. But yes, IoT is constructed that way … With signals to actuators that will result in altered sensor data feedback. Know the actuator signals, and the actuator-to-sensor formulas (!), and you’re good to go towards full control, with good or bad (take-over) intent. Know either (or how to get into the sensor data stream), and at least you can destroy integrity and hence reliability. [DoS-blowing the signal away in total blockade or grey noise wipe-out, and your cover is blown as well. Is a single-shot or semi; you may want to have full-auto with the best silencer available…]
Hm, the above from the tinkering with the grand IoTAuditing framework promised… To turn this all into a risk managed approach. Well, for now I’ll leave you with:

[It has a glass floor up in there, you know. Blue Jays territory, ON – and yes, a very much sufficiently true and fair horizontal/vertical view picture, according to accountants]
IoTSec from IAM at entry to the end node
Now that you all are so busy implementing Internet of Things pilots everywhere, I mean at home like with this and this, but B2B everywhere as well (…!?) or are you doing it there not too, we may need to consider Security.
Yeah, Hans Teffer did a great piece on that (see here, in Dutch) and I blogged about that before [and many more links/posts…]. And, there’s quite some other issues with IoT. But the point here is – we haven’t thought of security before implementation.
And at the very few implementation’lets of IoT we see so far, security seems absent. Of course, you’d first want to make it work in the first place. But you’re doing it not right at the start, and you know that decisions made now (implicitly) will remain in the architecture for decades to come, in particular when today’s (almost) stand-alone implem’s become linked up into one giant uncontrolled, uncontrollable mesh.
Now, first, an intermission:

[At dawn]
So, ‘we’ all have been complaining about the security risks of IoT here and there and everywhere, in particular re the current risks of all sorts of industrial control being hooked up to the ‘net without anyone knowing or caring about proper sec.
And still then, we haven’t progressed beyond this Boy Crying Wolf position. Instead of moving to provide solutions. To begin with architecture ideas, the kind that we will need in order to branch out of the simpleton pilots.
On a walk, it struck me that one major part of any solution would be with Identification, Authentication (A1), and Authorisation (A2) – in particular at each and every end node in the network, the kinds you would want to reach to transit back to the Real, Physical world of Things and which are supposed to move ever closer to some form of smart dust… Whereas now, we often have the I and A1 usually at the front door, and the A2 somewhere in the/a network usually ‘near’ the end point (which also usually, is a relatively compute-enabled ‘large’ thing like a server with data).
Clearly, with the IoT we’ll need something else. All end points may float around somewhere out there, uncontrolled, un-tied-down in the giant global mesh network architecture. We will be systemically unable to tie any A2 server to an end point or vice versa (smart dust, spread out, remember), and the IA1-part will also be much, much less definable than it is today. But then, we’ll need much finer-grained access control at the end point, and much more flex at the (IA1) entry point or we leave it all free for all and only at the end point, the destination, check IA1 (again). For this IA1A2 at the end point, we need to consider:
- The end point(s) will very probably have very limited computing capacity; even with Moore et al., this will still lag required resource in a big way – because any type of ‘attack(er)’ will have vastly more computing power available. Hence, things will need to be really really simple at this point. We may need to consider global IoT mesh network segmentation or other pervasive and comprehensively secure forms of IA1 at entry points (how to guarantee complete coverage) or throughout the mesh (how to prevent complete coverage without even the slightest possibilities of evasion).
- Identities… ?? Where, how to manage the I’s and maintain the I+A1’s privacy, and transparency to the A2-owners ..?
- How to arrange A2 at all those end points, including the ability to maintain those ..? The dust (or some coarser-grained proxy, whatever) is out there, and can’t easily be uploaded all with the latest A2 tables we’d want – or that is done by some broadcast flash approach which is all too vulnerable for cracked use.
But still, we need something of that kind. And transparency built in to that, too… To ensure No Backdoors and accountability in general, as these cute little hidden holes would be exploitable by all the bad guys (official, and not). By the way, #ditchcyber.
I’m aware there’s more problems than solutions in the above. But you should be aware of the risks of letting them remain unsolved. Your suggestions, please!
And, just so you know:
RT @kauf: A Map of Every Device in the World That's Connected to the Internet http://t.co/t9RiPnwy0M pic.twitter.com/3ChTGRjWKC— GertJan Bos(@besocialonline) September 19, 2014
Old mass education
Everyone under 18, and anyone 18 and older, needs a massive re-schooling in all things new.
Yes that includes the savants that can hack (99,9% of which is just script kiddies, more on that below), and it includes those that may be slow learners due to age.
But first, a picture:
 [Pfanner, Lucca]
[Pfanner, Lucca]
The subjects to mass re-school for:
-
Programming of all sorts. Not just CSS/HTML. Also, perl/PHP, SQL, C, Prolog, etc. Etc. Etc. From fundamentals (yes indeed) all the way to slick quasi-savvy app programming. To know what’s under the hood, to be able to work in the field, at all ages to one’s level.
Oh, and let’s not forget all would need to know how to configure a network, and how to secure it. - Design, that is such an important part of Making things these days.
- IoT and 3D printing (see the previous ones coming together?), for the future; to be able to navigate and play an active role. Otherwise, masses get isolated and out of anything resembling jobs. If you can’t operate in tomorrow’s society, if you can’t do anything worth a living wage, you’ll be cast out.
- Ethics and sociology, in particular re privacy, the coming Singularity, and World problems like global warming, waste and environmental destruction, and resource depletion. Whether by Augmented Humanity or full humanity oblivion, the future comes to us too fast to first see and then adjust. All now present may NOT defer this to others. You ARE all the others like never before.
- And all that we know already. All science, humanities, etc. Because schooling has lowered its standards so much. Having more and more (%) in ever ‘higher’ education but teaching less and less. Overall, isn’t coping with society and its complexity the sum total aggregated goal of education ..? Where society has become so much more complex than it was; exponential growth in this one, too has not been dealt with in Ed, on the contrary. Re-creating a plebs. Of all shapes and sizes, including moneyed plebs. The latter seem to rule… I’ll come back to this issue, later. Book by Quote’s pending…
Hey, it’s just a matter of survival beyond mere bare physical needs, for the very near future of all.
And, how to educate all ..?
- Through gaming, of course
- Through non-gaming rote learning all the essentials as well. Otherwise, you’ll fail miserably in practice when reality somehow doesn’t quite conform the game show. Which it won’t for decades to come. And no, shallow learning will not work; if only because it’s not learning at all.
- Through gaining reality experience, of course in the course(s). As application is everything also re turning ratio learning into experience and control.
- Through in-depth specialisations, to all sorts of levels and breaths. As almost all (except the very, very few script/kit builders) of today’s hackers are script kiddies and the ‘markets’ in that area continue to develop, some knowledge and experience may actually get lost! No, the ‘net does not ‘save’ everything; information production is just too large every day for the storage available globally…
-
All this delivered in traditional classrooms, mixed with MOOCs, mixed with interactive self-learning in class or at home or elsewhere. Which means teachers will have to be re-schooled too, if only because a too large share of them already are backward, too lowly educated (in content) laggerds. As in:
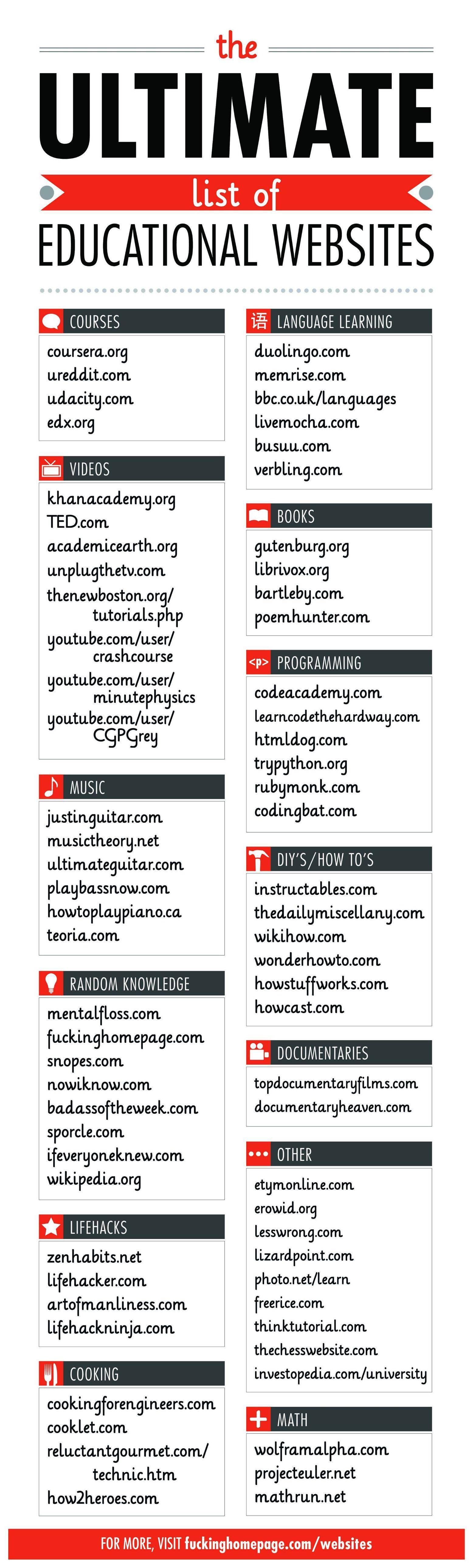
What a task for society. But if ignored, the amount of ignorance will just be too big for the world to handle. Your comments, please.





