Remember, that (not) a great many days ago I posted some bits on crypto ..? There’s a new twist to it all, after the venerable Bruce noted that some agency started a new, this time ’round bit more fundamental round, on crypto algorithms. And then, some notes on the approach of quantum computing. Well, the latter is still five to ten years off (current estimates; could be three, could be twenty, as such estimates go).
But impacting. So, the following flew by:
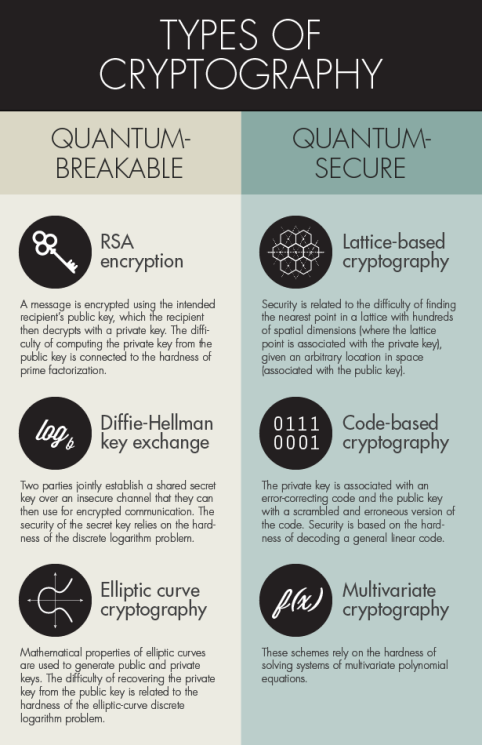
Which explains a lot, hence I just wanted to pass it on. Bye for now.
Tag: Risk Management
Trivial TLA Things-Tip
If you Thought This Time Things would be easier, as the universality of plug-‘n-play has spread beyond even the wildest early dreams into the realms of the unthought-of non-thinkingness, think again. Drop the again. Think. That was IBM’s motto, and they created Watson. No surprises there.
However… It may come as a surprise to some that now, an actual TLA has some actual tips, to keep you safe(r). As in this. Who would have thought… On second thought, this agency of note might have no need for the access disabled themselves anymore, as they’ve provided themselves of sufficient other access (methods) by now and just want to hinder the (foreign) others out of their easy access ..?
Oh well, never can do well, right? And this:

[Another one from the cathedral of dry feet — only after, making sticking fingers in dykes worthwhile; at Lynden, Haarlemmermeer]
Let’s celebrate (with) a contest for the dumbest security
On this celebration day (for me/us), let’s instate an annual contest — over the most precise prediction of the dumbest information security breach of the upcoming year.
So, the following:
- Your prediction, storified (½ – 1 page, at most slightly formatted);
- Realistic, i.e., a combination of dumb and dumber, and stupid and worse, of (non)actions and responses, on the attack and ‘defense’ sides. Realistic, but keep it realistic…;
- Hence, do include lots of cyberhere, cyberthere, cybereverywhere and only a little bit of #ditchcyber …;
- Deadline: 1 January 2016;
- The predictive element means that no sign of the thing actually occuring yet, may be found in the (whatever medium) press already;
- Prize… ah, there you go. I’ll try to figure out a way to ship a bottle of the finest champagne to the winner;
- No discussions about my judgement.
Well, off for now. Have fun:

[Shaky ground (huh, just photographer’s lack of proper alignment due to hurry);
somewhat relevant, in the opposite (of today)]
Cyber ‘Nam
OK… As you know I wouldn’t be the war monger re ‘cyber’ warfare. And don’t have the answers — neither do you! — but have searched and asked for them; see past posts (numerous).
This one is more about how the campaigns and battles are fought. Full cyberstatefulfirewallcomplexmonitoringNOCSOC jacket style, out there in the field. (Privacy) protesters at home, safely away from the danger. Some top brass (‘generals die in bed’) ordering your data forward, hardly trained/hardened or crypto protected and blaming shoddy execution and wily counterparts. The traumatised demobilised db admin not wanting to shoot down even a deer-like referential integrity violation. Et cetera. Feel free to add to the comparison. E.g., how things will develop. Or– how thing would have to work out if, huge if, for once history is learnt from.
Oh well. @CyberTaters and @cyberXpert will have their way. And #ditchcyber. And this:

[Will be.]
Sharing a name for economy
Rightfully, I thought as I read this article… but then, not.
Yes, ‘sharing economy’ is abuse by the UburbNb’s of this world as they’re exploitative scams that have little to do with the actual Sharing Economy.
The actual Sharing Economy is about sharing because of caring, which is price-less in itself and holds quite some anti-monetary ulterior goals.
The Sharing Economy shouldn’t have to change its name because others, in an ethically-horrendous and despicable robbery, claimed it.
And all this is futile resistance. “All that is of value, is defenseless” (Troelstra)
And:

[Yes, the same as a couple of weeks ago, now from a approx. 120deg different angle, still works ..?]
Ebow to lower prices, up the sharing ec
OK, here we have these two trends:
- Ebay still being around (although slowly, coming under attack from entrants; check your feeds if you’d have missed that) but when people get tired, they bid lower and lower, when at the same time sellers want decent prices or retract and retreat. A fair market may not exist after all – or it is the minute details that turn out to count.
- The sharing economy is growing, steadily.
So, the two may go together. One doesn’t get enough on Eb and rather give it away, resulting in less traders and trades on Eb closing the circle. Not a virtuous one. But would anyone care ..? And, data please!
For those in the kno:

[Art. My own. [Mostly unedited indoor phone pic]]
Industry tourism
… not the other way around. Or, both.
Where the most afford-able tourists will ‘move on’ to ever newer places when things get too crowded, or just too common, they will in the end return to past favourites, when the wind of stampedes has blown over. Industries … do the same ..? Considering IoT is really turning manufacturing’s global movements and spread on its head, with the AI in-roads leading to e.g., a switch of human involvement from ‘hands’ to ‘brains’ [what a change! managers should fear …!], I wanted to start some economics analysis here but don’t have the right data at hand.
So, for the series, I’ll explore. Like, cycling from primary all the way to quartary (?) industry (administrationland), and back (and forth) in between, innovating as we go along … no, no this post is going nowhere. Must be Friday’s.
Similarly, I have no clue why this [own] anonymous Philly pic is here. Or is my account hacked and did some joker just put the above down as a claim ..?

Keezel: Online freedom
De administratie is van geen van allen … [Dutch]
Was triggered by this here article, as read in het Parool but repubd – and deserves republication in many more places. Yes it’s in Dutch unfortunately, as I don’t think the problem is exclusive but it may be tearjerkingly worse and exposed here…
Waar nog bijkomt dat een flink aantal (?-tot-100%) ‘bestuurders’ nog steeds in de illusie leven dat ze iets ‘besturen’ en dan ferme besluiten nemen, met de vuist op tafel slaan zelfs, en dat er vervolgens niks gebeurt. Helemaal niets. Het ‘besluit’ was immers de prestatie *quod non* en de uitvoering, tsja, dat is voor het lagere volk. Daar ga je je niet mee bezighouden. Terwijl het besluit zó ver los staat van de werkelijkheid lees implementeerbaarheid (op wat voor manier dan ook; taalgebrabbel los van normale praktijk, met bij voorbaat zeker gierend budgetgebrek) dat niemand zich waagt het op te pakken. Dus *gebeurt* er niks…
Als je dat maar eventjes stil kan houden (fijne wensmanagementrapportages in bestuursjargon ja We Zijn Nu Eens Echt Goed Bezig Met Actiemaken maar niet heus), dan is het Na Ons De Zondvloed. De naam ‘Asscher’ gaat rond in het Groene-artikel. Wel goed dat er een enquête komt! (of al voorbij is gezucht zonder dat iemand er erg in had). En oh wat goed dat die wordt gehouden door dezelfde in-crowd; dan weet je zeker dat er iets echts uit gaat komen..! </sarcasme>(?)
Maar ja, er schijnen zelfs nog mensen te zijn die werkelijk denken dat we in een democratie leven. Als de facto een pak ‘m beet 0,0001% van de stemgerechtigde bevolking uitmaakt op wie je überhaupt kán stemmen en geen enkele partij de moeite neemt om te zorgen dat je het met meer dan maar 30% van de standpunten eens kan zijn (waar de rest persoonlijke hobbietjes zijn; belastingmiljardenverslindend en vaak nutteloos) met een persoonlijke aansprakelijkheid van nihil, terwijl “dan richt je toch zelf een politieke partij op” niet kán werken, ja dan heb je een echte democratie hoor ..!
Passend:

[Actual government, direct; tranquil reflection on that]
#ditchcyber CSI, this was real
A quote, a post:
This is a story of a very high-tech kidnapping:
FBI court filings unsealed last week showed how Denise Huskins’ kidnappers used anonymous remailers, image sharing sites, Tor, and other people’s Wi-Fi to communicate with the police and the media, scrupulously scrubbing meta data from photos before sending. They tried to use computer spyware and a DropCam to monitor the aftermath of the abduction and had a Parrot radio-controlled drone standing by to pick up the ransom by remote control.
The story also demonstrates just how effective the FBI is tracing cell phone usage these days. They had a blocked call from the kidnappers to the victim’s cell phone. First they used an search warrant to AT&T to get the actual calling number. After learning that it was an AT&T prepaid Trakfone, they called AT&T to find out where the burner was bought, what the serial numbers were, and the location where the calls were made from.
The FBI reached out to Tracfone, which was able to tell the agents that the phone was purchased from a Target store in Pleasant Hill on March 2 at 5:39 pm. Target provided the bureau with a surveillance-cam photo of the buyer: a white male with dark hair and medium build. AT&T turned over records showing the phone had been used within 650 feet of a cell site in South Lake Tahoe.
Here’s the criminal complaint. It borders on surreal. Were it an episode of CSI:Cyber, you would never believe it.
Just to remind you; it’s not all APTs only that hit you. Here, it was ‘just’ hardcore kdnapping. And think about victims of false … [fill in your favourite of the four horsemen of computer crime and colour the picture] accusations alone: Defamation by the clueless, works at much longer terms, and maybe more effectively. Nothing progressive, innovative, disruptive about that… And:

[Yes that is the First Flag – government project: (i.e.) unfinished]






