
[Your prospect of Elysean fields]
2019 is only five years away… But predictions require a suitably close horizon to be able to see how today’s trends and Early Indicators might play out, and still be sufficiently distant to allow flexibility and variance off the predictions – otherwise the predictions are dull.
Hence, apart from my predictions for 2014 (and update) below, some more ‘mega’trends, in particular for the management of information risks – I still maintain that anything managed, isn’t a risk ‘anymore’! – professional or more specifically, the ‘information systems auditor’. Note the ‘’ as this post will show how the role and content will change enough to warrant a new job title.
Now then. As a starting point, I took the insightful graph of the always even more insightful Ross Dawson off rossdawson.com, noting the CC-BY-SA 2.5 license:
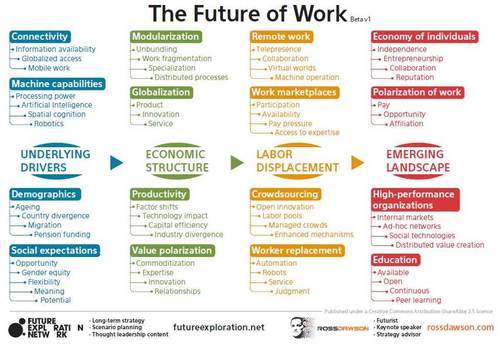
Which is a depiction of trends that impact the IS auditor as professional, rather than touching (too much) on the content of her/his work… Indeed, but I’ll demonstrate where the content is touched, too, by the trends depicted. Let’s just run them down one by one:
1. Connectivity will mean the necessary re-think of the traditional CIA to be able to guide, control and audit the information security stance of clients. The Information availability explosion, the globalised (i.e., de-geography-bound is de-accidental-physical-location-bound) access hence globalised use, and mobile work to even loose the ties of the Last Mile (in a way), require this. And enable the IS auditor to do the same. Already, this is being piloted, and in my view, we’ll see much more of this kind of work for the IS auditor in the very near future; this enables not only the auditor to not have to come to the clients’ offices too much – albeit that initially, some F2F contact may still be required but the need may diminish quickly when clients gain experience –, it also enables her/him to engage with clients much further afield, remotely. As far as (by today’s standards) superb connections reach, that is. See items 5, 9, 10, 13, and 15 below.
2. Machine capabilities will lead to work being taken from our hands. Through raw processing power explosions (not only due to Moore, but also due to the explosion of the sheer number of devices out there), Spatial recognition giving machines even more data to deal with, and large-scale Artificial Intelligence deployment not the petty trials of today, will enable the off-loading of much manual mental work (human- / person-bound work) to machines ‘out there’. The user will not even need to know where the ‘there’ is. Or should (s)he ..? We’ll see a redesign of philosophy, thought, methodology and tools on privacy surface. Quite some areas where IS auditors might (sic) lead the way, in thinking, acting, controlling and auditing.
And robotics … If that takes off, it’ll be piecemeal on the one hand (I too want my Roomba) but massive on the other (so many disjoint markets blooming). If only Asimov’s Three Laws can be reinstated, and reenforced or we’ll end up either in a mess or dead… It’ll start with Worker replacement anyway … (see below).
3. Demographics are something that we have somewhat less to deal with in the management of information risks. Apart from Migration leading to professionals’ markets impoverishing to markets of lemons, if unprotected (the dams will only hold back only so much inflow for only so shortly), and Country divergence maybe hitting us when our geographic region forces us to move elsewhere, as in item 1 above.
4. Social expectations Not much, either, apart from the Flexibility that will created Theory of Firm 2.0 type organisations, on which the IS auditor and others can no longer impose totalitarian bureaucracy. What then ..!? I don’t know. Your bad, if you can’t adapt… From the true ethics of your trade, you should have already adapted long ago…
5. Modularisation may impact us in ways similar to what we have already seen in the past; just labour specialisation, if any. Not too much to do about not too much. Though the general trend by which broad experience by and large caters for broad, balanced widening of one’s professional content in the stages after specialisation, may turn or have been turned already, the direction is unclear, either repeating constantly all directions, or awaiting a major redirection.
6. Globalisation I already characterised as a possible major impact through the Connectivity angle. In Products, I consider it to will come to completion in the near future. Service… To the degree that any service has no physical-presence component; (medical) care, for one, would be hard to do remotely, and also some other personal services e.g., IT tech support, may not ever work to a satisfactory degree without being able to communicate by nonverbal / sensory signals. So, not all the promises of item 1 above may not be realised all too soon.
7. Productivity will be driven by the Machine capabilities, mostly. Together with Connectivity, theese will determine Factor shifts or rather, define and refine factors of worth. Manual labour will re-flourish! And so will brain work, but only the non-standardised stuff, the work requiring creativity, true intelligence and empathy. Where many IS auditors etal. Think they are, but they aren’t. You know my rants against ‘peers’ just checking boxes. That is not what auditing is about. That is administration. Auditing, and other management of risk roles (sic), is about interpretations, judgement, close calls, gut feeling, and guts. Balls. (F/M), you must have them or be replaced by drones. Do not count on being (just) on the right side of the dividing line! Count on being on the wrong side, the down side, the cast out side. Or join progress.
8. Value polarisation again one where the machine capabilities, Connectivity, and Globalisation will work to quickly create new classes of haves and have-nots. The 1% of today, may be another 1% in other fields tomorrow or the day after. Try to be part of that, or you’re no longer suitable as part of life. Seek out your own 1%. But one thing would clearly be wrong: Remain as you are, meek, sheepish, not daring to be a Man (M/F) … So, most IS auditors et al. will have to change dramatically, if one can change one’s character…
9. Remote work I already described above. Telepresence, (remote!) Collaboration, and (local) Machine operation – 3D rinting, maybe ..? – will work as above (item 1 again). Virtual worlds may provide diversion from the destroyed natural habitat we still have to live in. The tropical island scenario still is somewhat too far away from us.
10. Work marketplaces are the mechanism through which the market for lemons may play out, or not. The barriers to Participation should be watched – some arguments for, some against –, Availability may not be an issue anymore (oh, but availability of suitable, sustainable markets may be), Pay pressure defines the lemons aspect, as does Access to expertise. Don’t sit still, as through Globalisation, access to expertise and availability, and participation will lead to pay pressure. I.e., pressure on your economic sustainability. Do not think you’re protected in your behemoth Organisation; any organisation is not too big to fail ..! So, even Big4 IS auditors should be aware. The bigger, the … no, size doesn’t delay a crash landing into a gentle glide, you’ll not be able to sit it out. The only sliver of new work would be to assess the work marketplaces against some standard but even that may be outsourced to … why assume a certified auditor should do that; why not instead (sic) by a reliable professional …
11. Crowdsourcing will impact IS auditors, too. But it may be a threat, or a blessing. No more dumb production of checked boxes…!? On the one hand, drafting those dull IS adit work programs from PDFs and too lengthy texts, may be outsourced to Labor pools – lucky if you can stay out of them, otherwise, you’re done. Will you be the one overlooking Managed crowds, or in it? By the munbers, and by today’s mentality, the vast majority of IS auditors will in fact be in the masses. Enhanced mechanisms will enable evenmore IS audit work (aspects) to be crowdsourced, changing the value proposition in the audit / advisory projects hence threatening livelihood. Open innovation’s also an In or Out aspect, for IS audit work. Though there may be a splinter of secondary audit work to be done on the deliverables of crowd sourcing and on the crowd markets… Fuzzy why that should be by certified auditors.
12. Worker replacement. Oh yes, if you’re a worker. Which is what a lot of IS auditors are. Not doingthe hard to replace physical work (taken over by Robotics, see 2, for the standard stuff but) since this requiresproximity and flexibility. Plumbers will be OK, IS auditors, not; will suffer from (enormous progress in) Automation, Robots, though Service may be slower to migrate (medical care robots may be proficient in many other areas, too, though), and Judgement may be the last to go over, to AI. So, as above, anything requiring judgement may for the foreseeable future not be taken away from us. But again, so many IS auditors et al. don’t judge, but administer. Where would you want to go, if (not when!) you would be able to (quod non)..?
13. Economy of individuals I consider to regard our profession in particular. Are you one of those few ones above that actively seeks out one’s own future? Then you’re in luck; your Independence and Entrepeneurship may lead to work being available, in Collaboration of the Theory of Firm 2.0 based on your Reputation. All these factors will be currencies of the future, so work on hoarding them! Not ‘the’ currencies, as Bitcoin and the like may kick in on a large scale within five years.
14. Polarisation of work With the Pay and Opportunity being so unevenly distributed, one may not rely on Affiliation with an organisation of old any longer. The dinosaurs are dying. New affiliations will need to be sought out. IS auditors, be aware, be active or be left out.
15. High-performance organisations or as I indicated above, Theory of Firm 2.0 organisations, may rise quite quickly. Google, Facebook and the like have risen to their 1.5 (sic) status and size in (qua order of magnitude) five years. Others may be in their inception phase today, and be the biggies, the most wanted (virtual) workplaces literally tomorrow. Again, be aware. Internal markets, Ad-hoc networks, Social technologies and Distributed value creation may all be part of the landscape of small and middle-sized temporary organisations that will flourish, already from, literally, today and tomorrow on. All these factors point at project-oriented get-togethers of professionals all with their own needs (for fair value to contribution distribution) and wants (work only where, when and for whom you like, do only what you like; if one factor starts to fail, move elsewhere) banding together just for the common interest and then all going their own ways again, maybe meeting again in the future, maybe not. Temporary Affiliation only..? Or looser ties? Double o, though many an IS auditor may have a single o as they haven’t innovated and are left behind as deadwood.
16. Education is key, to many of society’s desirable developments. Available, Open, Continuous is must be, and focused on Peer learning. All things where IS auditors could play a role, as auditors and advisors, and partaking out of necessity to keep abreast of latest developments.
Because the italics weren’t there for nothing. IS auditors, and others, just play a role and not an important one at that! Do not fool yourselves; auditors are only, and no more than, an afterthought of business and other organisations. Be happy that you have some specialised knowledge that you apply in whatever role, one accidentally being audit. When now both the unimportance of the audit role comes to the fore, in particular through Ross Dawson’s megatrends and technology developments, and your knowledge and experience that you apply in the role, are ever quicker to expire, you’ll have to keep abreast of all new knowledge ever more certainly, ever more widely and completely, and ever faster, and you’ll have to constantly seek out new roles to apply your greatness. Dropping audit as an expired old skin…
The central message is clear. IS auditors et al.: Innovate! That takes trial and error, and ‘learning experiences’ also for one’s deeper insights and even character, it takes risk taking and damage to one’s personal quest(s), but with the right virtues (Aristoteles-like), one will prevail. Innovate, along the lines of the work future and towards developments as described elsewhere and more.
[More will follow on this subject…]
















