Wow, the new year starts of with … failure. I mean, apart from your inability to keep your New Year’s resolutions (already – if you need such a specific date like Jan 1 and the motivation of a ‘fresh start’ which, on the whole, it isn’t since calendars were invented as easy shorthands not life (so exactly) defined turning points) to change habits, … why didn’t you just change when the need arose ..? You’d be much further with it – the year is really off to a traditional start when failures of the past, are repeated ad nauseam… [As interlude: No, writing shorter sentences isn’t and wasn’t on any of my resolutions’ lists…]
Which one might expect from less-clear thinking professions. Though this post isn’t meant to address the precious few, the exceptions to the rule, I do mean ‘accountants’ and ‘IT-auditors’ (IS auditors that don’t understand) to be among those. That, apart from the slew of other vices you can easily sum up, tend to instruct others to do risk analysis this way:
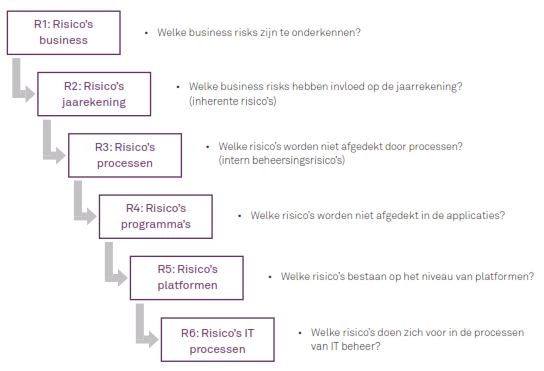
Yeah that’s in Dutch but you probably can make out the (actual) content and meaning. Being that the risk analysis is (to be) carried out top-down indeed, analyzing how lower layers of the model will (have to) protect against risks in the layers above, after the controls at any layer may have failed to ‘control’ the risks… [About that ‘control’ quod NON: See this here post of old.]
See? This just perpetuates the toxic myth of top-down analysis. The more one would follow this model, the more deluded one’s risk estimates would become… And this is proposed to lead the way in financial audits…
If you think this limits the Spectre of errors – this thinking permeates, and will permeate, the audit / inspection environment, leading to ‘Sony’. Yes, this erroneous thinking is at, or near, the root cause of that mess-up. [Anyone has seen proof that the NK actually did it, I mean, not the ‘proof’ trumped up by the most biased party ..?]
Whereas a bottom-up approach would show all the weaknesses that would create logically impossible effectiveness of higher-up ‘controls’. Controls just aren’t put in place to build a somewhat reliable platform to build higher-order controls on… Controls are put in place to try (in vein) to protect same-level risks throughout, as well, and higher-level controls were (are; hopefully not too much anymore) put in place to try to protect against all the lower-level controls failures not remediatable there… [‘Mitigation’ as the newspeak champion]
Hence, the distribution of error ranges (outside the acceptable sliver in the middle of the distribution of, e.g., transaction flows – hopefully that sliver is the intentional one) is ever wider the higher one goes in the ‘model’.
Rightfully wrecking your approach to financial audits, where not the risks of misrepresented true and fair views are managed, but the risks that the auditor is caught and found guilty of malpractice by not doing the slightest bit of the checking promised. ‘Assurance’ hence beginning with the right first three letters. Risk management to cut down the enormous workload (due to the overwhelming risks percolating up the model, as in reality they do..! hence having to check almost everything) to nicely within the commercial cutthroat race-to-the-bottom budget which is supplanted with ridiculously attractive (by bordering(!?)-on-the-fraudulent hourly rates) consulting business.
Now, the only hope we have is that the R6 model will not spread beyond … oh hey, googling it returns zero results – let’s keep it that way! Let’s not follow BAD guidance…
Jeez… And that’s only two of 124 pages of this…
I’ll leave you with …
![20141101_155144[1]](https://maverisk.nl/wp-content/uploads/20141101_1551441.jpg)
At the door to
![20141101_160525[1]](https://maverisk.nl/wp-content/uploads/20141101_1605251.jpg)
– if you know what these are, you know why they’re here…
 [Odd shape; maybe off-putting as a defense mechanism ..!?]
[Odd shape; maybe off-putting as a defense mechanism ..!?]



![20141101_155144[1]](https://maverisk.nl/wp-content/uploads/20141101_1551441.jpg)
![20141101_160525[1]](https://maverisk.nl/wp-content/uploads/20141101_1605251.jpg)
![20141027_131258_HDR[3]](https://maverisk.nl/wp-content/uploads/20141027_131258_hdr3.jpg)










