A slight update to the previous post: What I propse in the end isn’t as much a shift to qualitative risk management as such, but an even further step to intuitive risk management. Yeah, that’s fuzzy. But doable. And will boil down to the sort of ‘real’, normal management that leaders-managers have already practiced throughout the centuries (and certainly in the better parts of the 20th century).
So no worries, the future isn’t all certain but that makes it fun, right ..?
Category: Information Risk Management
The 15.5 risk
Your 15.5 risk is of no interest at all! I have a 15.6 risk! Hm, I only have a 13.1
Seriously.
You know you’re doing that. But will you admit it, and learn, and move to something better ..?

[Hi, DC!]
There’s a lot wrong in risk management today. I mean, not only can one still rant about the ‘three lines of defense’ (quod non) as I do regularly on this blog, but one can also dive into the details of how risks are managed, if not when, and find a lot of systemic error and particularly, non-thinking all around.
Let’s start with one core element: weigh(t)ing and comparison of risks. With my guesses, based on decades of experience and science/literature:
Do you include all risks, or just the tiny fraction that your mind can get a hold of? My guess is: The latter. So you miss the vast majority of the risk universe and will be grossly incomplete.
Do you include upside potentials (actions unthought of, and uncontrolled/unsmashed by measures) too? My guess is: No, again you’re incomplete, but also you’re so biased I can’t trust you anymore.
Do you use High-Medium-Low for impacts? My guess is: Yes. Or you use 1-5 scales or so, maybe (sic) even with sort-of indicator thresholds or brackets to determine what goes where. But you don’t realise that impacts can vary, very much so and in time, too. Averages will not do in subsequent calculations or other analysis! You must have (continuous!) impact functions of time and chance. If they’re hard to establish (I’d say: Impossible, given the scarcity of data!), that’s your bad.
Do you use High-Medium-Low for probability (frequency expectations)? My guess is: Yes. Or you use 1-5 scales or so, maybe (sic) even with sort-of indicator thresholds or brackets to determine what goes where. But you don’t realise that probabilities can vary, very much so and in time, too. Averages will not do in subsequent calculations or other analysis! You must have (continuous!) probability functions of time and impact. If they’re hard to establish (I’d say: Impossible, given the scarcity of data!), that’s your bad.
Do you know the difference between statistics and chance calculus? I guess not. Hah, and then you still abuse both ..? Do you know the difference between discrete and continuous mathematics (functions)? If not, you’ll make errors all around. How would you arrive at a 15.5 score when all choices are discrete 1-5 …?
And if you notices the duality of impact functions of probability, and probability functions of impacts; you’re welcome. And if you noticed that on top of this all, you should also calculate (sic) for the cost (impact) of pre-emptive, detective, corrective etc. measures, and the chances of their partial or full (in)effectiveness, in a mesh of cause and effect.
Do you use Impact X Chance to establish severity of risks? Guessed so. But unless you take the whole continuous (!) two-dimensional landscape of every risk into account, you’re gonna fail with certainty.
Do you compare relative risks by their combined scores? Yeah, that indeed was the whole purpose of your exercise. But you failed already on so many points, the results are both literally and figuratively ridiculous
And you continue by considering a ‘15.5’ risk to be worse or higher than some ‘15.4’ risk….
And you don’t consider the enormous mesh of causes and effects (just one by one, or per single event only) with all sorts of feedback and feedforward loops, and the mesh of ‘preventative’, detective and corrective mitigating measures in between, all with their distinct cost(impact!)s, mutual reliance, reinforcements or and other influences, all with their inefficiencies and ineffectiveness (sic) levels – in percentages? In number of incident elements caught and missed?
We may continue. But it’ll lead to more of the same; you’re fooling yourself, and fooling decision makers. Didn’t know that that was in your job description. What would you think would happen if the decision makers would find out?
And oh yes they will! You lead them astray so much, that they will find (you) out about plain wrong negative impact times frequency totals in Write-Offs, and when (not if) they’ll dig deeper, find quite a lot of unnecessary, inefficient and ineffective Risk Mitigation Measures Overhead Cost.
Is there another way? Yes of course.
But it’s not easy. It takes the European (vis-à-vis the wrongly dubbed Anglo-Saxon) approach where the focus is not on data but on qualitative scenarios. As with data, these can be had externally, or internally from experience and insight. As with data, external inputs can be of doubtful relevance and fit. As with data, internal input may (in case of data: will!) be (much) too limited to work with. And yes, going through the motions to determine some risk on all four areas (external vs. internal, data vs. scenario) and finding some gross common denominator, one can get a balanced view on things. But it’ll be balanced over four erroneous outcomes; way to go!
If the outcomes will be understood at all. Value At Risk being the case in point, that would better be called Amount of Company Value Not Being Lost At Some Random Probability. Or so, depending on your working definition and working understanding of VaR…
The only solution seems to be to stop using a quantitative approach and switch to a radical qualitative approach. This may be awkward, but quantities are just so much too weak to describe reality that they are a fly in the face fraud.
And indeed, we we don’t know how to do organisation-wide qualitative risk analysis and management let alone how to do it for meso- and macro-levels, let alone how to communicate, understand and argue about one risk to the next. But we have nothing else that can work; we must. And, it may fit better with the way humans, the human brains, work, with all their psychological ‘flaws’ (quod non!) in the management of risks. Kahnemann, remember? Well, maybe to align with what our brains have gotten used to handle over the aeons, from the savannah to our latter-day deserts of cubicle offices may be the best way to go. And why not? Do you really want to argue that today’s offices differ from hunter-gatherer tribes batteling the elements, predators and prey, and other tribes?
So, qualitative management of risk it is. Any takers?
Fraud, try angle it differently
The fraud triangle should be not more. For too long, the simpleton representation of fraud occurrence possibility has dumbed down the discussion about countermeasures too much, leading to an unwanted, unwarranted, inefficient and ineffective approach difference from various sides.

[For those who know where this is: This is unconnected to the story ;-]
Point being: The fraud triangle, being one where the three factors Motive (or Pressure), Rationalisation, and Opportunity are presented as if present at the same time, and banding together. Take one of the elements out of the equasion and you’re good. But the three factors do not play out at the same time.
Rather, they play out consecutively, leading to a false sense of security when only one is addressed as even the wiki page on fraud deterrence suggests.
Wrongly! Because e.g., when Opportunity is taken away, as if most often the ‘easy’ solution in organisations, Motive and Rationalisation (the formers start it, the latter coaches it) will find another way as the pressure of Motive will rise and rise until somewhere else than the valve installed, some crack or so may burst, or the whole kettle may explode.
[Damn! Here, I had a perfect, really perfect two A4 pages full of text that disappeared in a glitch… The rest you see here, is just a bleak re-do missing the brille of the original… No, the re-write is not better than the original. Thanks, Tumblr! [Insert hard expletives here]]
As Motive is the thing that comes first, it should also be the first thing to address. It starts with not giving too much motive, which is the same as giving all your employees a reasonable compensation for their efforts that starts with the paycheck. In particular in hard economic times, some or many of your employees may heed more to their ethics (!) and provide for their family before sticking to stupid rules of some big anonymous organisation that doesn’t really know who they are and what their pligh is. Ethics, yes, that thought discipline that is about having to decide between the conflicting rules of various groups that any human is part of. Family, friends, etc., and the organisation one might feel part of – or not, or not enough to let organisation group belonging outweigh familiy group belonging when it comes to a showdown, e.g., when they feel they don’t get their due but just the alms you so graciously hand them for your own grandeur only.
And if you’re visible to the public at large (and you will be, however you try to protect your image) as having so much more than your staff has, family etc. may start to actively pressure your employees to get up close to that level. You’re pushing them yourselves! Inequity forces (no, not less than forces) employees into a getting-even motivation..!
Both ‘hard’ and ‘soft’ pressures to get even, play out in the Motive element, but also in the Rationalisation element. Rationalisation is nothing else than the rationalisation of the ethical decision that your unconscious mind already made, for when your consciousness might turn up again later.
Let alone that it may not only be such ethics that force employees into less following the organisation’s stupid little rules. Think of what would happen if a family health or life is threatened by rogues; this happens all the time. But you can’t have all your employees and their family being secured all the time; they will leave you all as no-one can life under such circumstances of total siege.
And you do need to care for all employees, as all have access to possibly Opportunity-instrumental information. Do not think that you org chart or top-down approach may work, at all. That would miss (literally) 99% of all the information flow that goes through your organisation, and 99% of the paths that the information takes. You think your ‘processes’ are your organisation? Think again, think the opposite!
Which ties in with the Opportunity part. The Opportunity may be everywhere, at all organisation levels, in all sorts of combinations of petty-little-rule breaking or ‘sticking to the little rules so you can break the big ones’. You simply cannot know all the ways and places, and times, that Opportunity for fraud may exist. If you think that simple things like encryption may help then yes, they may help, but so little, so very, very little. As if IT staff, and masses of others, would not know their way around it. And any dam creates its lake that will overflow and create much more damage; the pressure is not diminished by the dam!
So, you can’t do much about Motive, Rationalisation, or Opportunity. Not much, a little bit.
Which is where we may take a look outside of the totalitarian control bureaucracy world I led you into above, which is typically today thinly veiled under a ‘Risk Management’ layer (just this morning saw an article discussing that we don’t need Risk Management, we need management of risk…!], or under the label ‘risk-driven information security’ etc. All wrong approaches, panicky seeking total control.
All we can do, then, is to sand off the rough edges. Which is what is done already, by (physical) Security as it has been done through the ages. Just take a look at a sample table:
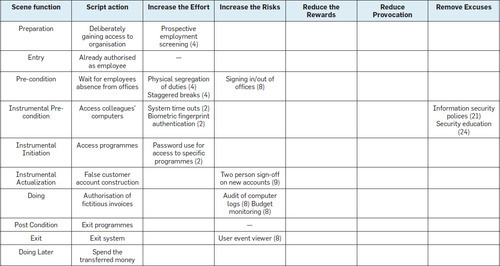
It’s easy to see how this can be filled in to cover many more angles and available tools of information security, and can be expanded to cover much more of your organisation’s business. And it’s also easy to see that e.g., not all information security should be had only from IT measures, and not all process/procedural opportunity should be lessened by procedural refinement only. Cross-discipline measures could keep it all much lighter!
But just look at the last five column headers… Much better to approach fraud prevention through those than just sticking to Motive, Rationalisation, Opportunity, right? These ‘solutions’ may not prevent each and every fraud, but they keep things in check. If that’s the most you can get, then be happy with it!
More, maybe, later, on filling out the table in all sorts of situations.
Is ID you?

[Guess the location]
Your digital ID becomes your pseudo-identity becomes who you are (considered to be), more than your actual you.
Your actual you, your innate identity, the one you discovered when only a couple of years old, will no longer be of interest to the world once your digital identity has all that the world cares about. Then, it can get stolen, lost, manipulated and altered, without you actually needing to notice. But who cares? Your digital ID is, you are just the carbon-based remnants of an outdated world. Just make sure there’s a fallback scenario that you can (or wouldn’t need to) prove you are you, your digital ID isn’t you.
The singularity may do away with you because you only use up scarce resource. You are not productive, your digital identity is. So you should care. Or?
If social media use ‘you’ as a resource, uses your apparent digital ID (ID and all posts, tweets, etc., turned into a persona, sold to all bidders) to operate, can you not deploy some artificial intelligence mechanism to do the socmed postings on your behalf ..? What’s the difference to the socmed companies that not your brain, but an artificial brain is used ..? Or do they already have their own farms of AI personas, to beef up traffic and sellable ‘user’ generated content ..?
Their AI personas may create a world separate from yours, a virtual world where they make money, not needing actual users anymore.
Your personal self may deploy AI to detach from their abusive, you-usurping world.
Case closed?
Why not Necker ..?

[Surprise in the (business) heart of Paris La Défense]
With all the hype about BYOD and the New Way of Working, flexible work place etc. having died down almost to zero, why are we still in offices ..? Why aren’t we all (…?) more like @richardbranson also for our working lives?
We certainly had the time to build a suitable infrastructure where there was none, if only under the guise (as it often is) of helping development (to the ideal level of material-only development that we have ..!?). I mean, cheap or free fast WiFi on any and all tropical beaches. Then, we could al have moved there and live a re-engineered happy life.
Oh, and we would have had to change the way we organise, and manage and control, work. Just a detail. The question seems to be: Why haven’t we?
Probably because of massive societal (level) fear of the Unknown. No, not fear of losing control, that’s just part, and one side, of it. We fear the loss of our warm, established social environment more than the gains of a warm, physically beneficial environment. Even if the gains are larger than the losses (that may be partial or replaced, in this case), fear drives more than hope (risk aversity).
Which may be overcome by the individual, by the minority that does venture out of the cave (see some earlier blog entry). But there, one might fear being the single odd one out, losing before gains could be had. Hm.
Or we could consciously take it step by step, starting with actual telework, videoconferencing etc. not immediately on a massive scale, just one by one (huh) or in small organisational communities. We need more of these dust grains in a supercritical fluid!
And at the same time, organise work better, bottom-up, in a sea of temporary collections of independent professionals banding together for a common goal (and with respective gains distributions) and then dissolving once the job’s done (project over, even if the project lasts decades like even blue chips are on average gone in half a century), to new ventures elsewhere.
Will we return (?) to a world where work is no longer life’s almost-single purpose but is maybe something bothersome just to earn the money to buy breathing space all the way down and up Maslow’s pyramid, and is something that caters to the higher levels of that so that all talent is expressed and rewarded ..? Looks like a ‘first world problem’ — hence one that can be solved!
Control, not privacy

In the discussions re privacy, there seems to be only two alternatives: Absolute privacy, with any individual holding complete, total and continuous control over who gets to see (not take in) any data point that may be, even in the remotest of ways, be recombined into anything useful for anyone – or Absolutely no privacy, everything being considered lost anyway and all one’s data being out there somewhere.
Which creates not some binary future state, but a bandwidth on which we should be able to choose. Because it is not privacy that people are concerned about, but the loss of control once data slips out of your hands. That is why everyone is so concerned when TLAs are found out to collect so much data on everyone (they have tried, and partially succeeeded, already for decades; nottoo many people were concerned) or when (not if) yet another credit card data processor looses some backup tapes. It is not the privacy in itself (one passes off the credit card number (and CVC) happily to just any unchecked device), it is not being able to get the data ‘back’, not being able to track the use in all the enormous amount of systems one knows is out there handling your data. Those systems ranging all the way from the benign to the crooked, always …
What we should have, then, is some mechanism by which we would be able to transparently and trasitively (sic) release the data we must (in order to get some service in return), and be rewarded for any data other parties earn money with (they are using your resource!), and not more. We’ll have control back; all we wanted.
Anything else, and we’ll end up in one of both extremes. To our own extreme detriment.
Inter faces

[Educational institute x 3, campus Free University, Amsterdam]
When sleeping over problems, one often comes up with solutions that both are real and so all-encompassing that they’ll need much elaboration before being applicable in a nimble way.
This one was/is on information security, again. Recall the ‘discussions’ I posted some days ago about (industrial) process control versus administrative control? Well, I’ve some more elements for a grand new scheme now.
It struck me that the operators at the (chemical) plant control room, are the ones with the dashboards. Not necessarily their managers. Nor their manager managers, etc. What if instead of some machine equipment, we plug in hoomans into the whole ..? And let them interact like the übercomplex ‘machines’ that they are, doing their (administrative / service) thing that they (want to?) do. All the way to the point where we have no equipment, just humans (with tools, by the way, but those would be under ‘complete’ control of the ones using them so are just extensions of them). One ‘manager’ could then control quite a lot; have a huge span of control…
If, big if, if only the manager would understand the overall ‘process’ well enough, that is, to be able to work with the dashboard then provided. Just Continuous Monitoring as a job, not much more (one would have 2nd- and/or 3rd ‘lines of control’ (ugh for the expression) to fix deviations, do planned maintenance, etc.). Probably not. But one can still dream; organizations would be flat without chaos breaking out.
And if you’d say it would be impossible altogether, have a look at your SOC/NOC room where techies monitor IT network traffic and systems’ health. They even have some room to correct..! And they are aware, monitor, the appropriateness of what flows over the lines, having professional pride in catching un(machine)detected patterns of irregularity possibly being break-in/break-out attempts. And they leave the content for what it is, that’s for the experts, the users themselves, to understand and monitor if only they would.
Why wouldn’t other ‘managers’ copy the idea to their own desk? No, they don’t, yet. They get Reports that they hardly read, because someone else had thought for them in determining what should be in there. And reports aren’t continuous. Walking around is, but would (rightly) be viewed as micromanagement and a bit too much given the non-continuous nature of what modern knowledge workers do. So, we’ll have to define some gauges that are monitored semi-continuously.
Now, a picture again to refresh:

[Westpunt, Curaçao]
But with the measurements not influencing the primary production ..! To let knowledge workers do their thing, in mutual cooperation without interference by some busybody thinking (s)he knows better for no reason whatsoever.
Through which we note that the use of dashboards should not, must not, start with ‘Board’s or similar utterly superfluous governance levels. Governance is for governments. As it is ‘implemented’ in larger organizations, it doesn’t look like kindergarten kids playing Important for nothing. The use of dashboards should start from the bottom, and should include quite rigorous (but not merely by the numbers) pruning of both middle-level ‘managers’ (keep the good ones, i.e., not the ones that are only expert in hanging on! otherwise you spell death), and all sorts of groupie secondary and third-line staff.
Which will only work if you haven’t yet driven out all the knowledge workers by dumbing down their work into ‘processes’ and ‘procedures’ that are bereft of any productive (sic) rationale. And if you haven’t driven out all the actual managers and are left with the deadwood that is expert only in toeing the line or rather, sitting dead still in their place.
Now have a look back also on how you do information security. Wouldn’t the little bit of tuning you may need to do, be focused best on the very shop floor level that go into the ‘industrial’ process as inputs? You would only have to informationsecure anything that would not be controlled ‘automatically’, innate in the humans that handle the information (and data; we’ll discuss later). Leave infosec mostly with them, with support concentrated at an infosec department maybe, and have managers monitor it only to the extent necessary.
And, by extension, the same would go for risk management altogether. Wouldn’t this deliver a much more lean and mean org structure than the top-down approaches that lead to such massive counterproductive overhead as we see today? With the very first-line staff that would need all the freedom feasible to be productive (the managers and rest of the overhead, aren’t, very very maybe only indirectly but certainly not worth their current income levels!) then not having to prove their innocence… See Menno Lanting’s blog for details…
Org structures have become more diamond- than pyramid-shaped; which is plain wrong for effectiveness and efficiency…
So let’s cut the cr.p and manage the interfaces, vertically, and horizontally, noting the faces part; human. An art maybe, but better than the current nonsense…
Predictions 2014; little update

[Paris La Defense; Metropolis-like]
Oh, a few notes to add to the Predictions 2014 blog:
Just saw that Smart, Cloud, Analytics and Mobile may abbreviate quite well… T not fitting in there…
Forrester (-‘16) rightly adds a rethink of ‘trust’ and ‘identity’
Gartner has ‘software defined everything’ and ‘3D printing’ in the mix. The former, Forrester has as well, when reading and recombining what they have (and G’s predictions may be regrouped as well, to form the F’s list, or the SCAM-T list).
Both don’t have Analytics, oddly enough. But via @duivestein, too, a good intro into Things.
Maybe we’d include Trust, Identity, Things abbreviated, before SCAM.
Back to predicting, I expect to see some hitherto unseen early signals re the dissolution of the absolute governance power of geography-bound countries / nation-states, and the nascence of (more) virtual communities with some form of barriers. Remember what I dropped as a note below on Bitcoin; I expect to see more of those in(ter)ventions. Interesting to see how the power balances (multiple) may play out: Will some developments be kidnapped / abused by states in a global (cold) cyberwar e.g., via or in the UN; how will the developments resist, and what will hold or not ..? This, too, may not be a thing for 2014 only (it may take decades!), but we’ll see some buds spring up next year.
That’s all. For now. Whether that’s Now, is another discussion entirely.
Predictions 2014
Already somewhere below, I noted that the Analytics part of SMAC(T) may need to be rephrased. Already now, I’m unsure whether to do that or just leave it unchanged. What I didn’t yet do, was to opine on the other elements so often put together.
First, a picture.

[Casa de Música Porto, for the chaotic structure of the future]
Now then:
Social everything: Yeah, yeah, of course there will be news. The decline of Fubbuck, etc. But will we see actual breakthrough hitherto unseen inventions of anything game-changingly new? I predict 2014 will be a pause year in which we’ll only see paradigm detailing and quite an improvement (sic) of the use of Social by medium- and larger sized enterprises. In somewhat innnovative ways, but nothing earth-shattering.
Mobile everything: The same, hopefully through the much-wanted huge improvements in cross-platform and cross-screensize compatibility and standardization. Which, too, would be refinement rather than absolutely unexpected New.
Analytics, we discussed, separately.
Cloud, ‘mehhh’ for theory, ‘hey how refreshing to be able to distinguish so clearly a good implementation’ in practice. Because that’s what we’ll see in 2014; cloud stuff deliberately done right. (Being deliberate, not by accident as it was in 2013!)
Things; The Internet Of ~, maybe, but in my view it’ll be too early. More like something for under the [Warning: European + derivative culture reference coming up] Christmas tree, to be played with in the year after.
Any other business?
Yes.
One with long odds: Clarity on the demise of “ERP” software. Of course, pre-2014 already the said administrative software, hardly ever used to its full potential but very often having been relegated into the bookkeeping role only, had been pushed away from the limelight into the back of the stage. But in 2014, we’ll see an acknowledgement of this, with consequences I cannot really predict very well – probably, all sorts of other software, more geared towards front-office functionality and integrating better architecturally with the bandwidth from there to the app/widget-world, will take over center stage.
[Update 2014 02 06: This link]
One with lesser odds: An enormous push for more information security, both at its operational, technical levels and upwards in renewal of structure (away from the stale, outdated ISO2700x sphere!) and inclusion of a more holistic approach (see some of my earlier posts, and probably some to come in the near future).
This will have a second leg in renewed interest in Business Continuity Management, not only by rule-based following of standards but also by more principle-based (sic) implementation of ISO 31000 (with all its drawbacks) throughout the business. If we can get our heads around the eradication of that ‘the business’ nonsense… and really integrate (continuity) risk-based management into general management, not needing too much 2nd or 3rd lines:
A final one: The deflation of TLD. The three lines don’t actually defend against anything but regulatory discovery of all that goes wrong in the business (from top to bottom and back again, there). As the previous prediction will already defend against actual mishaps, TLD will be shown to be emperor’s new clothes where lightning strikes. And oh will it strike; frappez, frappez toujours! it will and I hope. All those busybodies doing busywork, I just can’t stand it. The utter denouncement of humanity and human dignity …!
So, there you have it again; SMAC(T) weighed, and three more. Who make some interesting stuff available when I hit (or overshoot) five or more out of eight ..?
To close, another picture…

[Serralves, Porto – rainy outlook]
Invitation: Responsible disclosure for charities
Staking a claim, and asking for your input! (Again…)
First, a picture to brighten up your day:

[Sevilla, obviously]
There have been many rows in public discussion regarding the spend of charities. Either the moneys received haven’t been spent according to expectation (sic), or the charities’ governors have received (perceived (sic) to be) too high recompense for their efforts and/or costs.
Common denominator is of course lack of transparency upfront that could have set expectations better, and would have demonstrated due diligence and due care. This, beyond the formal bookkeeping disclosures of annual accounts, etc., that apparently are too opaque for the public to understand. Or even for the guardians of public interest; journalists.
So, the invitation is to contribute to a little research study projectlet I’m starting, on responsible disclosure for charities.
To find a model or pointers, by which charity governors may increase transparency towards the general public about the spend of money, without having to cough up all detailed private income data or having to distort sound (fund) spending strategies.
And with sufficient clarity to all, if possible even the dumb masses (not derogatory, but sometimes they appear to be…). This may be a challenge; to clarify strategy without having to cast it in stone and/or dumb it down itself into forseeable ineffectiveness.
First up: Benchmarking governor’s incomes from the charities. E.g., vis-à-vis others’ hours put into the charities, and/or hourly wages. Would that be possible? What would be the standard? (Since simple numbers would lead to a race to the bottom in governor quality!) Etc.
So, any contribution takers …?





