
[Meant as gateway, not closure]
Earlier, as in here, here and here, and other places apart from these, I floated the idea of redesigning the way we tackle the core of Information security. Unfortunately, I don’t have sufficient time (yet!) in lunch breaks to get it all together in one big white paper hence I’ll drop some elements here, again.
I’ll keep working on collecting loose ends, so when I find time, I can integrate it all, including your comments, of which I have received so much. Not so much. As one. Single. Comment.
Herewith, then, to start off, a picture I took from … somewhere, probably the ISACA site somewhere. I’ll work from this, structuring the story line from top to bottom, first how we do it now (kindergarten level, with the pretense, pomp and circumstance of high priests doing high art), next, how it should be done ndash; qualitatively, vaguely, massaging off the rough edges and not being able to do much more except for the hardest cores of security (Remember the pyramid I presented? Read up via the above links).
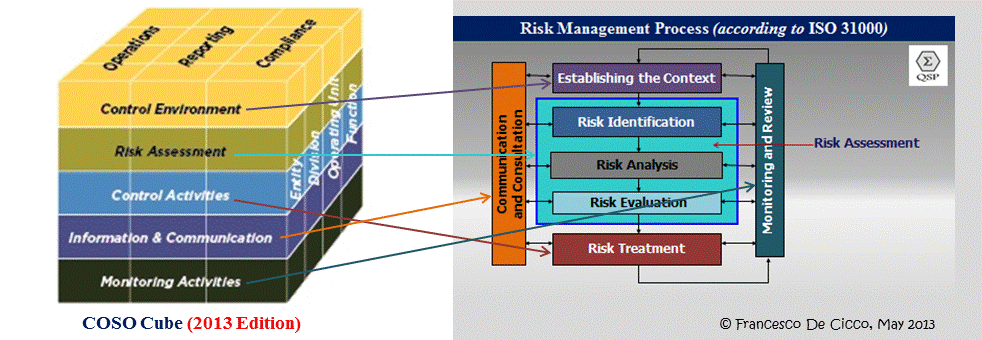
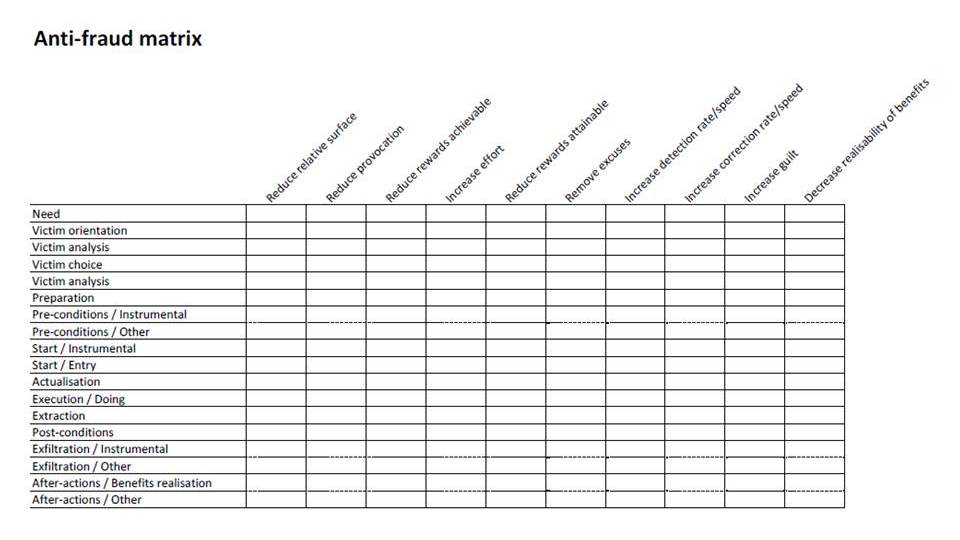
Also, I’ll drill down a bit on the design of controls, according the lines sketched earlier (yup, see links again) and using an augmented [By me; disclaimer [Huh? When it’s by me: Why …!?]: *value may not be included] anti-fraud matrix à la:
Which will have an advice that visually is something like this, of course:
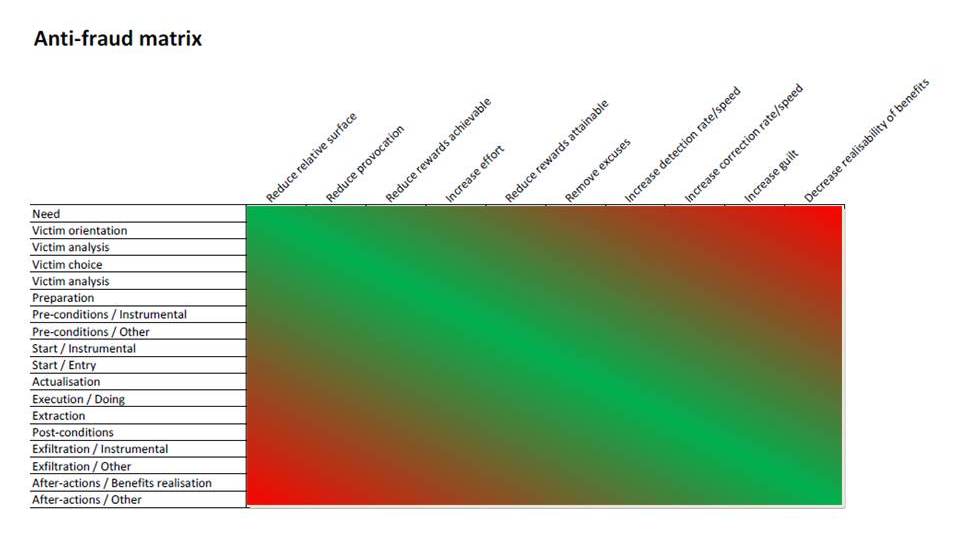
which is very different from the usual “Uhhhh, dunno, do we have a Motivation or Rationalisation here, dude..? Can’t progress until we figure out.” i.e. is design and action oriented.
But then, this matrix will be overlaid (third dimension) on the SABSA matrix I guess. Though I’ll make it very clear that SABSA is all very well, but very much focused on the bottom layers of itself only, the bottom layers of the InfoSec pyramid I sketched. And, upwards, there’s much methodological confusion. In particular re its Information and Conceptual / Context / Wisdom definitions and placements.
And of course I’ll throw in a bit of ABAC referring to this.
OK. Time’s up!
Which means I welcome your comments. One may dream, right …?





















