There may be more reasons that quantum crypto will not protect you against those evil villains out there, as suggested here (in Dutch) but quod non!!! (as I said; in Dutch ;-| ), for the not ten but one single reason:
When ‘hackers’ will not be able to access your comms when you will be using quantum crypto, so governments will also not so forget about it you will be jailed for life for using quantum crypto in the first place and also you are the most suspect of all and if still you’d try to use it, you will be whacked off-line … and your house raided, etc.etc. Because this.
And because, however clever you might think you are, obviously in vein, there will always be the ‘endpoint-to-you gap’ where parties may intervene.
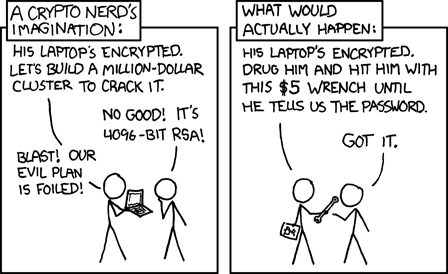
Or they put a gun to your head. Good luck refusing.
And governments will restrict to their own comms; the most powerful one grabbing the scene and leaving all of the rest in the dust. And IF you believe their beneficial ethics, well you just removed yourself from serious discussion.
Anyway:
 [Drone with too much tilt shift, or ’70s display scanned from an (actual, physical) slide..? (mine; ed.); <undisclosed location>]
[Drone with too much tilt shift, or ’70s display scanned from an (actual, physical) slide..? (mine; ed.); <undisclosed location>]