Noteworthy. In one sense, a dilution. In another, a move to widespread adoption and acceptance. From which, probably, some unforeseeable, maybe even weird, whole new societal developments may spring.
And, for the heck of it:
 [Pre-1998 analog to digital, FLlW @ Bear Run obviously]
[Pre-1998 analog to digital, FLlW @ Bear Run obviously]
Category: Information Security
There’s hope
Though hope has never been solid business planning, as it is what’s left after all rational expectations and handles have vanished and only leaving it to fate remains, this move may, may have some impact in one way or another: Ello mutating into a PBC.
And, for the weekend:
 [We have a beautiful prize available for the first to locate this!]
[We have a beautiful prize available for the first to locate this!]
The two faces of digital transformation
Players, sides, too many – where’s the (over)view?
Apart from the #ditchcyber aspects, in the (sometimes somewhat sportsy, even) battle about control, or is it temporary one-upmanship, over the world’s communications, so many parties play a role, in such varying sizes, and operating for so many sides, sometimes multiple sides at the same time, sometimes without even knowing that, with the interactions playing at various topics and levels of abstraction and with varying scopes, time horizons, strategies and plans (quality), I could really do with some clarity. Some mapping, interactive or not.
Which all was triggered by this post on yet another singleton developer taking on, inactively!, some well-funded TLA.
Will have to dive into the detail of it all, but know that I’ll end up losing the helicopter view. How many similar developments are out there, known or not? What stages of development, of deployment, of maturity, of starting to crack and leak are they all ..? It’s a hard life, this keeping up thing.
Hence, you deserve:
 [As if moulded by a genetic algorithm, Porto]
[As if moulded by a genetic algorithm, Porto]
Steve and Tim went up the hill…
Aren’t recent developments around, through, by the brand just an amusing (?) sign of the times – the times being the same as ever: A (single?) sinus wave (or multiple smaller ones, stacked on a larger one (bigger wavelength and amplitude); wavelets sales) –, as in this piece and this one ..?
As the latter quotes: “This is not [irrelevant reference to a musicological drama; ed.], and should instead be remembered primarily as a monumental blunder by the tech industry.”
to which:
Bono has apologized about the automatic U2 download: http://t.co/5NzdkKfgWB
— Gizmodo (@Gizmodo) October 15, 2014
But the details aside, why didn’t many enough see this coming? Why did anyone expect continued excellence from any company, in particular one so hyped, so turned into a dangerous cult already ..? Whereas so far, every co has demonstrated to have a serious Best Before / use By / Sell By issue. Except the rare exceptions, noted for the exceptionality.
As in:
"The average lifespan of an S&P 500 company has decreased from 67 years (1920's) to 15 years (today)" @salimismail #ExponentialOrganizations
— Singularity Group (@singularityu) October 12, 2014
Adn also don’t forget these twelve wineries… Yes some are so common and/or famed still that you wouldn’t think they’d be so old and still be in the same line of business… [Thanks Wine Turtle for the post]
So, the expectance that something(s; probably multiple, of varying error sizes and (distinct) impacts) might go wrong in any near future, would have had to be raised already, and rise still further. Note that through fuzzy logic, this isn’t offset I think by lowered probabilities of doing things well…! This is just how fuzzy (business) logic works, sometimes…
[Edited to add: And then we find this… Strangely not built into the corp system]
So, Steve and Tim went up the hill to have their little fun, then Tim forgot by taking the blue pill and now…
 [What a once great name … Reims. Yeah, look it up, I’m not going to spell it out for you]
[What a once great name … Reims. Yeah, look it up, I’m not going to spell it out for you]
Arms reversion (flipping); your call
Would anyone have the official name for a tactics switch leading to a collapse of an arms’ race ..?
I was triggered by this recent post about some gang(s) using low-tech but somewhat-sophisticated pencil-and-paper crypto in stead of the highest tech burner phones etc. (or did they also use those). To which many commented that probably, the code should be (very) easily crackable even if all of the many safeguards were upheld.
(But also, dropping a physical USB stick at a (physical) watering hole (or desk, or handout point, or street corner pavement) also circumvents a great many fab network entry safeguards of the firewall kind, in particular when APT technology, stamina and dedication, and tailoring is involved.)
But then, what if the codes were good enough; time-based security still can work, and the adversaries (gov’t) weren’t overly capable in this, apparently. And one can also think back of what happened to the stealth fighter-bombers that suddenly showed to be vulnerable to detection by not the highest-tech radars but the decades old low-freq stuff e.g. the ‘Soviets’ had stored one day behind the Ural.
Sort of an arms’ race that has gone to such did-did not length that in the buildup, a sudden flip to old technique and old tactics / operations may undercut the sophistication of the other in an off-guard way. Maybe not allowable per arm wrestling rules, but arms’ races are a different ball game everywhere; no honour involved, weaseling allowed and winner takes all for the time being.
How would that be called..? Flipping? Reversion ..? I’m really interested. About your thoughts, too. E.g., how can one use this to improve security (‘pentesting’ yourself against such flips / reversions), on the Internet and elsewhere. Hope to hear!
I’ll leave you with:
 [A fordable river, at Cordoba]
[A fordable river, at Cordoba]
Regulation Renegation Abomi nation
So, after privacy-enhancing regulations finally got some traction here and there – mentally, hardly in implementation yet – we’re getting the full bucketloads of bovine-produced fertilizer regarding adapted protection through ‘Data Use Regulation’.
Which already throws back actual regulation in intent and in the letter of it. But has many more nefarious consequences… As is in this article; couldn’t word it better.
We should be vigilant …
IoTSec from IAM at entry to the end node
Now that you all are so busy implementing Internet of Things pilots everywhere, I mean at home like with this and this, but B2B everywhere as well (…!?) or are you doing it there not too, we may need to consider Security.
Yeah, Hans Teffer did a great piece on that (see here, in Dutch) and I blogged about that before [and many more links/posts…]. And, there’s quite some other issues with IoT. But the point here is – we haven’t thought of security before implementation.
And at the very few implementation’lets of IoT we see so far, security seems absent. Of course, you’d first want to make it work in the first place. But you’re doing it not right at the start, and you know that decisions made now (implicitly) will remain in the architecture for decades to come, in particular when today’s (almost) stand-alone implem’s become linked up into one giant uncontrolled, uncontrollable mesh.
Now, first, an intermission:

[At dawn]
So, ‘we’ all have been complaining about the security risks of IoT here and there and everywhere, in particular re the current risks of all sorts of industrial control being hooked up to the ‘net without anyone knowing or caring about proper sec.
And still then, we haven’t progressed beyond this Boy Crying Wolf position. Instead of moving to provide solutions. To begin with architecture ideas, the kind that we will need in order to branch out of the simpleton pilots.
On a walk, it struck me that one major part of any solution would be with Identification, Authentication (A1), and Authorisation (A2) – in particular at each and every end node in the network, the kinds you would want to reach to transit back to the Real, Physical world of Things and which are supposed to move ever closer to some form of smart dust… Whereas now, we often have the I and A1 usually at the front door, and the A2 somewhere in the/a network usually ‘near’ the end point (which also usually, is a relatively compute-enabled ‘large’ thing like a server with data).
Clearly, with the IoT we’ll need something else. All end points may float around somewhere out there, uncontrolled, un-tied-down in the giant global mesh network architecture. We will be systemically unable to tie any A2 server to an end point or vice versa (smart dust, spread out, remember), and the IA1-part will also be much, much less definable than it is today. But then, we’ll need much finer-grained access control at the end point, and much more flex at the (IA1) entry point or we leave it all free for all and only at the end point, the destination, check IA1 (again). For this IA1A2 at the end point, we need to consider:
- The end point(s) will very probably have very limited computing capacity; even with Moore et al., this will still lag required resource in a big way – because any type of ‘attack(er)’ will have vastly more computing power available. Hence, things will need to be really really simple at this point. We may need to consider global IoT mesh network segmentation or other pervasive and comprehensively secure forms of IA1 at entry points (how to guarantee complete coverage) or throughout the mesh (how to prevent complete coverage without even the slightest possibilities of evasion).
- Identities… ?? Where, how to manage the I’s and maintain the I+A1’s privacy, and transparency to the A2-owners ..?
- How to arrange A2 at all those end points, including the ability to maintain those ..? The dust (or some coarser-grained proxy, whatever) is out there, and can’t easily be uploaded all with the latest A2 tables we’d want – or that is done by some broadcast flash approach which is all too vulnerable for cracked use.
But still, we need something of that kind. And transparency built in to that, too… To ensure No Backdoors and accountability in general, as these cute little hidden holes would be exploitable by all the bad guys (official, and not). By the way, #ditchcyber.
I’m aware there’s more problems than solutions in the above. But you should be aware of the risks of letting them remain unsolved. Your suggestions, please!
And, just so you know:
RT @kauf: A Map of Every Device in the World That's Connected to the Internet http://t.co/t9RiPnwy0M pic.twitter.com/3ChTGRjWKC— GertJan Bos(@besocialonline) September 19, 2014
Cycle comments and questions
A certain commercial advisory club still releases its hype cycle. Which is good news; to have some authority with some authority (your mileage may vary) providing us with some comprehension and comprehensiveness [OK I’ll stop now] about the What’s Buzzworthy.
Still, being … in the field / Dutch / obnoxious, pick any; I’d like to comment…:
(Here’s the August version from … somewhere; ™ and © or what is it, acknowledged)
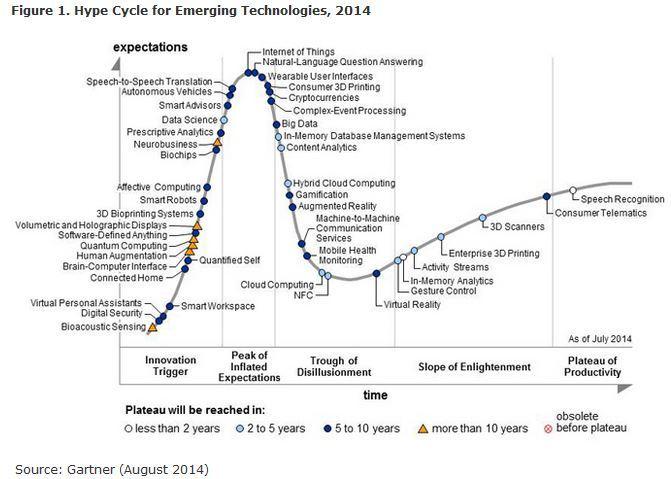
- Virtual Personal Assistants – 5 to 10 years out (of the plateau of productivity) ..? That’s optimistic ..!
- Brain-computer interface: If one would consider this to be about ‘intelligence’ connection, then maybe. But there’s also connections like hearing, et al., where a 5 to 10 year span may be on the ‘long’ side.
- Human augmentation: See the previous. Or aren’t definitions sufficiently orthogonal?
- Affective computing: Hm, optimists.
- Neurobusiness: Same.
- IoT: Yes, at a hype peak. Maybe (much) sooner, to be at the plateau.
- Cryptocurrencies: Hoping for a swifter spread and adoption…
- Big Data may be further down the slope already. Or is that from where I / we are ..?
- Gamification, augmented reality: Hopefully and quite possibly, already reality somewhat earlier.
- The rest of the bunch … will they not come sooner ..? Of shift shape (‘pivot’) to be unrecognizable from their today’s hype labels soon?
- And a final one: Would anyone have a similar overview of … one year, five and ten years back? Just to see what happen in the meantime; to establish a ballpark reliability figure. Would be fun, too.
I’ll leave you with this’all. Your comments are welcome(d). If you like to dream.
Managing Fortuna’s Risks
On how Risk Management is self-defeating… or just something one has to do while Life has other plans with you(r organization).
First, the übliche picture:

[Shadow (play) of Dudok, Hilversum again of course]
First, the Defeating part. This, we hardly discuss at length, full enough, but when we do, it’s so obvious you understand why: Because RM is about cost avoidance, even if opportunity cost avoidance. Which makes you the Cassandra, the Boy Cried Wolf of the courtiers (sic). It’s just not interesting, not entrepreneurial enough. [Even if that would be pearls before swines…]
Second, this is why it’s so hard to sell (no quotes, just outright sell for consultancy or budget bucks) the idea of RM to executives – they only see the cost you are. They don’t see themselves as delivering something if, if, if only, they had integrated RM into their daily ‘governance’ (liar! that’s just management!) / management. They don’t want to do anything. They just don’t understand to do something that doesn’t show to be effective even if others for once see no harm (though the others will not even care to flag the kindergarten-level window dressing that’s going on with the RM subject; too silly that, to call out).
Third, this happens not only with ‘boardroom’ RM (~consultancy/advisory), it has been well-established at lower ranks; all the way from the mundane IT security, Information Security, Information Risk Management, Operational Risk Management (where the vast majority of organisations don’t make anything tangible anymore), including the wing positions of, e.g., Credit and Market Risk (which are in fact, with the visors to mention, the same as the previous!), to Enterprise Risk Management altogether.
Fourth, we tie in Queuillism. The Do nothing part almost as in Keynesianism where in the latter, future-mishap prevention should be arranged during the years where government intervention wasn’t required as such. As in Joseph’s seven fat years contra the seven years of famine (Genesis 41). How does this reflect on RM? Would it not be just BCM in its widest, enterprise-wide sense? Isn’t that what ‘management’ is about, again..? Just sanding off the rough edges and for the rest, give room to the actual stars, the employees at all levels, to let them bring out their best – so exponentially much more than you can achieve by mere, petty, command & control. You raise KPIs, I rest my case of your incompetence. And this goes for governments even more. Just enormously expensive busywork.
Fifth, finally, the fourth trope points into the direction of Machiavelli’s Fortuna. Which was also covered by Montaigne, of course. It doesn’t matter what you do, in the end, Life has other plans with you. Sobering, eh? Oh but again, you can shave off the rough edges for yourself, too. Just don’t think in the end, that will matter much beyond some comfort to you. Katharsis, and move on.
OK, since you held out so long:
[The same, from another angle]






